Network operating systems (NOS) are the unsung heroes of the digital world, quietly orchestrating the flow of data and ensuring seamless communication across interconnected devices. Unlike general-purpose operating systems that manage individual computers, NOS focuses on managing and securing entire networks, providing a robust foundation for modern digital infrastructure.
Table of Contents
From the humble home network to sprawling enterprise environments, NOS plays a crucial role in enabling efficient resource sharing, implementing robust security measures, and facilitating seamless communication among users and devices. Its importance is further amplified in today’s interconnected world, where businesses rely on reliable and secure networks to operate efficiently and maintain competitive advantage.
Definition and Purpose
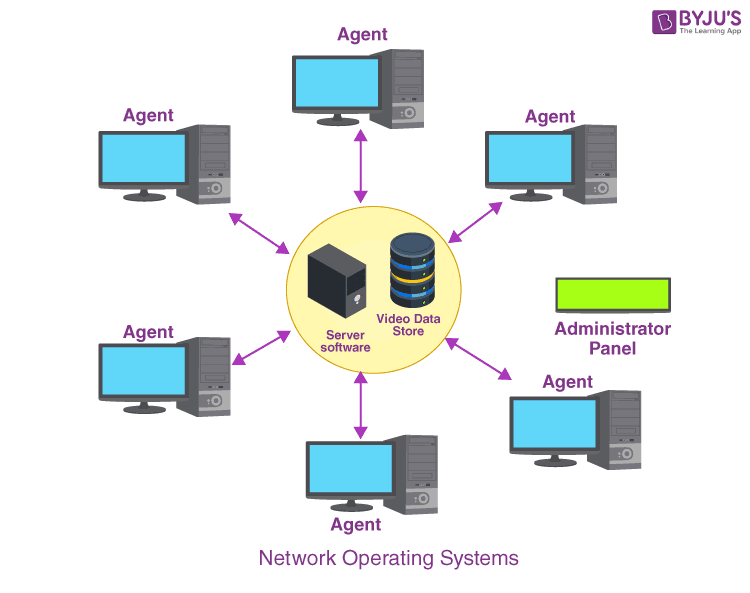
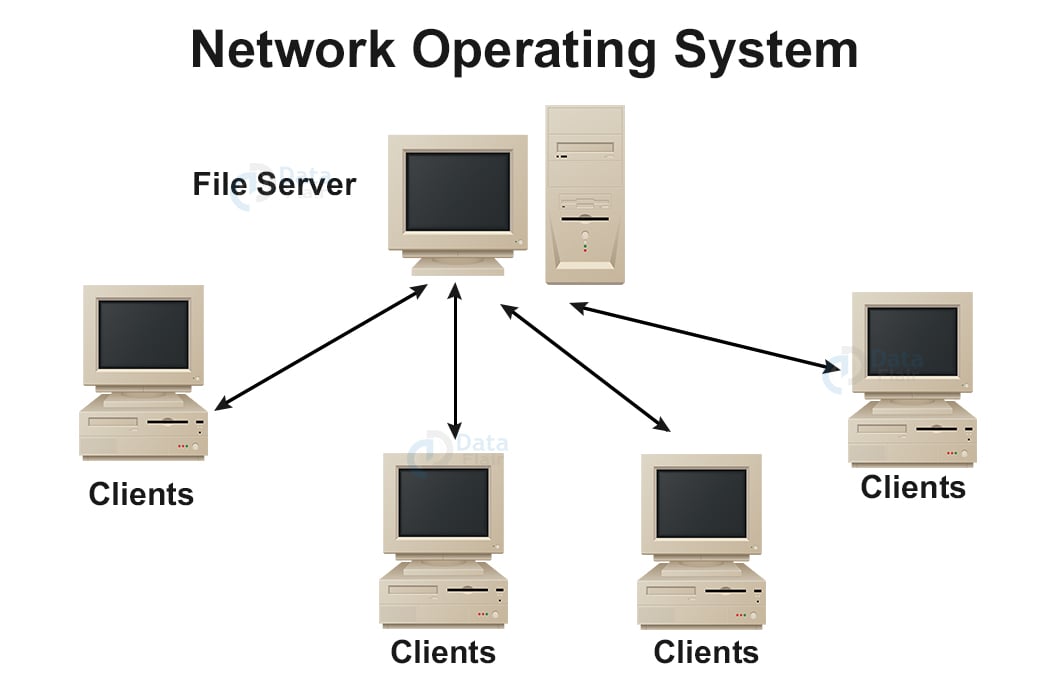
A network operating system (NOS) is a specialized software program designed to manage and control the resources and operations of a computer network. It acts as the central hub for network communication, ensuring smooth data flow and efficient resource allocation among connected devices.
The primary purpose of a NOS is to provide a robust and reliable platform for network connectivity and data exchange. It simplifies network administration, enhances security, and optimizes network performance.
Differences Between a NOS and a General-Purpose Operating System
The core difference between a NOS and a general-purpose operating system (such as Windows, macOS, or Linux) lies in their primary functions and target environments.
A general-purpose operating system focuses on managing a single computer’s resources, including hardware and software, while a NOS focuses on managing the resources and interactions of multiple computers connected in a network.
- Resource Management: A NOS manages network resources like bandwidth, storage, and printers, ensuring equitable access and efficient utilization by all connected devices. A general-purpose OS primarily manages the resources of a single computer.
- Network Communication: A NOS facilitates communication between devices on the network, enabling data exchange, file sharing, and application sharing. A general-purpose OS handles communication within a single computer.
- Security: A NOS plays a crucial role in securing the network by implementing access control, firewalls, and intrusion detection systems. A general-purpose OS focuses on securing the individual computer.
- Scalability: NOSs are designed to scale with the growing network size, accommodating more devices and increased traffic. A general-purpose OS is typically optimized for single-computer performance.
Real-World Scenarios Where a NOS is Essential
NOSs are indispensable in various real-world scenarios where managing network resources and communication is critical.
- Enterprise Networks: Large organizations rely on NOSs to manage their complex network infrastructure, connecting thousands of computers, servers, and other devices. They enable secure communication, data sharing, and centralized administration.
- Data Centers: Data centers, which house critical servers and data storage, heavily depend on NOSs to ensure high availability, redundancy, and efficient resource allocation. They manage traffic flow, storage access, and security measures.
- Home Networks: Even home networks benefit from the features of a NOS, albeit on a smaller scale. Routers and wireless access points often include embedded NOS functionality to manage network access, internet sharing, and device connectivity.
Key Features and Components

Network operating systems (NOS) are crucial for managing and controlling network resources, enabling seamless communication and data sharing among connected devices. They provide a range of features and components that facilitate efficient network operations and ensure secure and reliable connectivity.
Essential Features, Network operating system
Network operating systems offer a set of essential features that are vital for effective network management and operation. These features include:
- Network Management: NOS provides tools and functionalities for monitoring and controlling network performance, identifying and resolving issues, and managing network devices. This includes tasks such as traffic analysis, network configuration, and device management.
- Security: NOS plays a critical role in securing network resources and protecting data from unauthorized access. This involves implementing access control mechanisms, firewalls, intrusion detection systems, and other security measures to prevent cyber threats.
- Resource Sharing: NOS enables the sharing of resources, such as printers, files, and applications, among users on the network. This promotes collaboration and enhances productivity by providing access to shared resources from multiple devices.
Components of a NOS Architecture
The architecture of a typical NOS comprises several key components that work together to provide network services. These components include:
- Kernel: The kernel is the core of the NOS, responsible for managing system resources, handling network traffic, and providing essential services to other components. It acts as the central control unit for the entire network.
- Network Interface Card (NIC) Drivers: NIC drivers facilitate communication between the NOS and network hardware, such as Ethernet cards. They translate data packets between the NOS and the physical network.
- Network Protocols: Network protocols define the rules and procedures for data transmission and communication between devices on the network. Examples include TCP/IP, UDP, and HTTP.
- File System: The file system manages the storage and organization of files on the network. It provides mechanisms for creating, accessing, and managing files, enabling shared access to data.
- Security Services: Security services, such as firewalls, intrusion detection systems, and authentication mechanisms, protect the network from unauthorized access and malicious attacks.
- Management Console: The management console provides a user interface for configuring and managing network settings, monitoring network performance, and troubleshooting issues.
Comparison of NOS Features
The following table highlights the key features of different NOS, comparing and contrasting their capabilities in areas such as file sharing, print services, and user authentication:
| Feature | Windows Server | Linux (e.g., Red Hat Enterprise Linux) | macOS Server |
|---|---|---|---|
| File Sharing | Supports various file sharing protocols, including SMB/CIFS, FTP, and NFS. | Offers robust file sharing capabilities through protocols like NFS, SMB/CIFS, and FTP. | Provides file sharing services through AFP and SMB/CIFS protocols. |
| Print Services | Offers centralized print management, including print queues, driver management, and security settings. | Provides print services through CUPS (Common Unix Printing System), enabling shared printing across the network. | Includes print services that support shared printing and printer management. |
| User Authentication | Supports Active Directory for centralized user management and authentication. | Offers various authentication methods, including LDAP, RADIUS, and Kerberos. | Provides user authentication through Open Directory and LDAP. |
Network Protocols and Standards
Network protocols are the foundation of communication within a network. They define the rules and procedures that devices use to exchange data. Network operating systems (NOS) rely heavily on protocols to manage network resources, ensure data integrity, and facilitate smooth communication among connected devices.
Common Network Protocols
Network protocols play a crucial role in NOS functionality, providing a standardized framework for data exchange. Here are some of the most prevalent protocols employed by NOS:
- TCP/IP (Transmission Control Protocol/Internet Protocol): The cornerstone of the internet, TCP/IP is a suite of protocols that enables communication between devices on different networks. TCP provides reliable, ordered delivery of data, while IP handles addressing and routing.
- IPX/SPX (Internetwork Packet Exchange/Sequenced Packet Exchange): A protocol suite developed by Novell for its NetWare operating system. IPX/SPX offers reliable data transmission and addressing capabilities, primarily used in local area networks (LANs).
- NetBIOS (Network Basic Input/Output System): A protocol suite that enables applications to communicate with each other on a network. NetBIOS provides name resolution, session management, and data transfer services, primarily used in Microsoft Windows networks.
Protocol Interaction
Different protocols interact within a network environment to ensure seamless communication. For example, a web browser using TCP/IP to access a website on a remote server might utilize DNS (Domain Name System) to resolve the website’s domain name into an IP address. This process involves several protocol interactions:
The web browser sends a DNS request to a DNS server, which then resolves the domain name into an IP address. The browser then establishes a TCP connection with the web server using the IP address. Once the connection is established, the browser sends an HTTP (Hypertext Transfer Protocol) request to retrieve the web page. The web server responds with the web page content, which is then displayed in the browser.
Network Security and Management: Network Operating System
A robust network operating system (NOS) plays a critical role in safeguarding network integrity and ensuring efficient resource management. The NOS provides a comprehensive suite of security features and management tools to protect sensitive data, maintain network stability, and optimize performance.
Network Security Features
The NOS provides a variety of security features to protect networks from unauthorized access, malicious attacks, and data breaches. These features are designed to enforce access control, implement firewalls, and detect intrusions.
- Access Control: The NOS enables administrators to define granular access permissions for users and devices. This ensures that only authorized individuals can access specific network resources, preventing unauthorized data access or modification. For example, a NOS can restrict access to sensitive data servers based on user roles and department affiliation.
- Firewalls: Firewalls act as a barrier between the network and the external world, filtering incoming and outgoing traffic based on predefined rules. The NOS typically integrates a firewall that can be configured to block malicious traffic, prevent unauthorized access, and enforce security policies. A well-configured firewall can effectively mitigate the risk of external threats, such as malware infections and denial-of-service attacks.
- Intrusion Detection: The NOS often includes intrusion detection systems (IDS) that monitor network traffic for suspicious patterns or activities. These systems can identify potential security breaches, such as unauthorized login attempts, malware infections, or port scans. The IDS can then alert administrators to these threats, allowing them to take immediate action to mitigate the risk.
Network Management Tools
The NOS provides a comprehensive set of tools for managing network resources, monitoring performance, and troubleshooting issues. These tools enable administrators to optimize network efficiency, maintain uptime, and ensure optimal performance.
- Network Monitoring: The NOS provides tools for real-time monitoring of network performance metrics, such as bandwidth utilization, latency, and error rates. This allows administrators to identify potential bottlenecks, performance issues, or security threats. Network monitoring tools can generate alerts for critical events, enabling prompt troubleshooting and resolution.
- Resource Management: The NOS provides tools for managing network resources, such as bandwidth allocation, user accounts, and device configurations. These tools allow administrators to optimize resource utilization, prioritize traffic, and ensure network stability. For instance, the NOS can prioritize critical network traffic, such as voice and video communication, to ensure smooth operation during peak usage periods.
- Troubleshooting Tools: The NOS includes tools for diagnosing and resolving network issues, such as packet analysis, log analysis, and remote access. These tools provide administrators with valuable insights into network behavior, enabling them to identify and resolve network problems efficiently. For example, packet analysis can help identify network bottlenecks, while log analysis can reveal security breaches or performance issues.
Hypothetical Network Security Plan
Consider a small business with a network of 20 computers, a file server, and a website. To secure this network, the NOS can be leveraged to implement a comprehensive security plan that includes the following elements:
- Access Control: Implement strong password policies for user accounts and restrict access to sensitive data based on user roles. For example, employees in the sales department should only have access to sales-related data, while IT personnel should have access to all network resources.
- Firewall: Configure a firewall to block unauthorized access to the network, filter incoming and outgoing traffic based on predefined rules, and protect against common security threats. The firewall should be configured to block access to known malicious websites, prevent unauthorized remote access, and enforce security policies.
- Intrusion Detection: Implement an intrusion detection system (IDS) to monitor network traffic for suspicious patterns or activities. The IDS should be configured to alert administrators to potential security breaches, such as unauthorized login attempts, malware infections, or port scans.
- Network Monitoring: Monitor network performance metrics, such as bandwidth utilization, latency, and error rates, to identify potential bottlenecks, performance issues, or security threats. Network monitoring tools can generate alerts for critical events, enabling prompt troubleshooting and resolution.
- Regular Security Updates: Ensure that the NOS and all network devices are regularly updated with the latest security patches and updates. This helps to protect against known vulnerabilities and mitigate the risk of security breaches.
Real-World Applications and Use Cases
Network operating systems (NOS) are the backbone of modern networks, providing the essential infrastructure for communication, data sharing, and resource management. They are deployed in a wide range of environments, from small home networks to large enterprise networks, playing a crucial role in enabling seamless operations and supporting critical business functions.
Examples of NOS Deployment in Various Industries
NOS are indispensable in various industries, where they underpin the smooth functioning of operations and facilitate the efficient exchange of information. Here are some prominent examples:
- Healthcare: Hospitals and clinics rely heavily on NOS to manage patient records, share medical images, and connect medical devices. NOS ensures secure data storage and access, enabling efficient patient care and medical research. For example, a hospital might use a NOS to manage its network of medical imaging devices, ensuring that images can be securely transmitted and stored for diagnosis and treatment planning.
- Finance: Financial institutions utilize NOS to secure online banking platforms, manage financial transactions, and ensure the integrity of sensitive data. They implement robust security features and network monitoring tools to prevent unauthorized access and protect against cyber threats. For example, a bank might use a NOS to manage its network of ATMs, ensuring that transactions are secure and reliable.
- Education: Educational institutions use NOS to create secure and reliable networks for students, faculty, and staff. NOS enables access to online resources, facilitates collaboration, and supports distance learning initiatives. For example, a university might use a NOS to manage its network of classrooms and labs, ensuring that students and faculty have access to the resources they need.
Specific Scenarios Where NOS Plays a Critical Role
NOS play a critical role in managing and securing network infrastructure in various scenarios.
- Disaster Recovery: NOS are essential for disaster recovery planning, ensuring that critical network services can be restored quickly and efficiently in the event of a disaster. They facilitate the replication of data and services to backup sites, allowing for a seamless transition in case of an outage.
- Network Segmentation: NOS enable network segmentation, which divides a network into smaller, isolated segments. This helps to improve security by limiting the impact of security breaches and preventing unauthorized access to sensitive data.
- Virtualization: NOS are crucial for supporting network virtualization, which allows for the creation of virtual networks on top of physical infrastructure. This enhances flexibility and efficiency, enabling organizations to deploy and manage services more effectively.
Challenges and Opportunities Associated with NOS Deployment
Deploying NOS in complex and demanding environments presents both challenges and opportunities.
- Complexity: Managing and configuring NOS can be complex, especially in large and diverse networks. This requires specialized skills and expertise to ensure optimal performance and security.
- Security Threats: NOS must be constantly updated and patched to protect against evolving security threats. This requires ongoing vigilance and proactive measures to prevent attacks and data breaches.
- Scalability: As networks grow, NOS must be able to scale to accommodate increased traffic and demands. This requires careful planning and the use of scalable NOS solutions.
Concluding Remarks
As we delve deeper into the world of network operating systems, it becomes clear that their impact extends far beyond the technical realm. NOS is the backbone of modern digital infrastructure, enabling collaboration, innovation, and progress across various industries. Understanding the intricacies of NOS is essential for anyone involved in network management, security, and the design of robust and efficient digital ecosystems.
A network operating system (NOS) is a crucial component of any networked environment, managing resources and communication between devices. For data analysis and statistical computing, you might want to consider using R, a powerful programming language that can be downloaded from this website.
Once installed, R can be integrated with your NOS to provide enhanced data analysis capabilities, helping you gain valuable insights from your network data.
