Remote desktop monitoring software is a powerful tool that allows businesses to gain valuable insights into the activities happening on their employees’ computers. This software can track everything from keystrokes and websites visited to application usage and screen recordings, providing a comprehensive view of employee productivity, security, and compliance.
Table of Contents
From monitoring employee performance to ensuring data security, remote desktop monitoring software finds its place in a wide range of industries. IT departments can leverage this technology to troubleshoot technical issues remotely, while HR teams can utilize it to assess employee performance and identify potential training needs. Furthermore, organizations in highly regulated sectors like finance and healthcare can implement remote desktop monitoring to ensure compliance with industry standards and protect sensitive data.
Introduction to Remote Desktop Monitoring Software
Remote desktop monitoring software empowers organizations to oversee and manage their employees’ computer activities remotely. This software offers real-time insights into user actions, enabling businesses to enhance productivity, enforce security protocols, and troubleshoot technical issues effectively.
Industries and Use Cases
Remote desktop monitoring software finds its applications across diverse industries, catering to various needs and use cases.
- IT Support and Management: This software allows IT professionals to remotely access and troubleshoot user devices, ensuring seamless operations and resolving technical challenges swiftly. For instance, if an employee encounters a software malfunction, an IT technician can remotely access their computer to diagnose and resolve the issue without requiring physical presence.
- Customer Support: Remote desktop monitoring enables support teams to provide immediate assistance to customers experiencing technical difficulties. This can be particularly valuable for software companies offering remote support services. For example, a customer encountering problems with a software application can grant temporary access to a support representative, allowing the representative to view the customer’s screen and guide them through the troubleshooting process.
- Employee Monitoring and Productivity: Remote desktop monitoring can help organizations track employee activity and assess productivity levels. This can be beneficial for managing remote teams or ensuring compliance with work policies. For example, companies can use this software to monitor employee work hours, track website usage, and identify potential security risks.
- Security and Compliance: Remote desktop monitoring software plays a crucial role in maintaining data security and compliance with industry regulations. It allows organizations to monitor user activity, detect suspicious behavior, and enforce security policies. For example, financial institutions can use this software to monitor employee access to sensitive customer data and prevent unauthorized access or data breaches.
Key Features of Remote Desktop Monitoring Software

Remote desktop monitoring software offers a range of features that empower businesses to enhance productivity, security, and overall efficiency. These features provide valuable insights into employee activities, system performance, and potential security threats.
Remote Access and Control
Remote access and control are fundamental features that enable administrators to connect to and manage remote computers securely. This feature allows for troubleshooting, software installation, and configuration changes without physically being present at the device.
Real-Time Monitoring
Real-time monitoring allows administrators to observe ongoing activities on remote computers, providing valuable insights into user behavior, system performance, and potential issues. This feature can help identify performance bottlenecks, security threats, and user errors in real time, enabling prompt action.
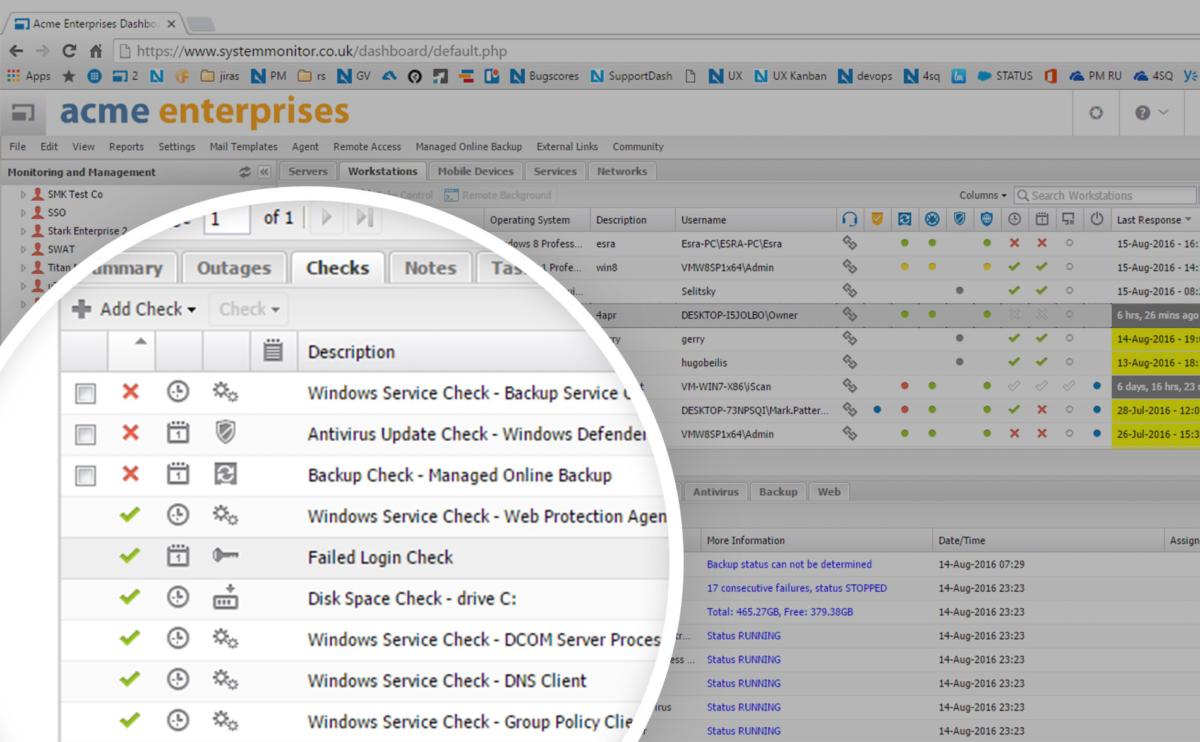
Activity Logging and Reporting
Activity logging and reporting provide detailed records of user actions, system events, and application usage. This data can be analyzed to identify trends, assess productivity, and investigate security incidents.
Screen Recording
Screen recording captures the visual activity on a remote computer, providing a comprehensive record of user interactions, software usage, and troubleshooting sessions. This feature is particularly useful for training, performance reviews, and security investigations.
Keystroke Monitoring
Keystroke monitoring captures every keystroke entered on a remote computer, providing detailed insights into user actions and data entry. This feature can be used to monitor employee productivity, identify security risks, and prevent data leaks.
User Activity Tracking
User activity tracking monitors user actions on remote computers, providing insights into application usage, website visits, and file access. This data can be used to assess employee productivity, identify potential security threats, and improve user experience.
Alerting and Notifications
Alerting and notifications inform administrators of critical events, such as system errors, security breaches, and user activity anomalies. This feature enables timely intervention and minimizes downtime.
Data Security and Compliance
Remote desktop monitoring software often includes features that enhance data security and compliance. These features may include data encryption, access control, and audit trails, ensuring data confidentiality and integrity.
Remote Device Management
Remote device management allows administrators to manage and configure remote computers, including software updates, security settings, and hardware configurations. This feature simplifies device management and ensures consistent security across the network.
User Management and Permissions
User management and permissions allow administrators to control access to remote computers and specific resources. This feature ensures that only authorized users can access sensitive information and applications.
Reporting and Analytics
Reporting and analytics tools provide comprehensive insights into user activity, system performance, and security threats. This data can be used to identify trends, assess productivity, and make informed decisions.
Integration with Other Systems
Many remote desktop monitoring software solutions integrate with other systems, such as ticketing systems, identity management platforms, and security information and event management (SIEM) tools. This integration streamlines workflows and provides a unified view of security and performance data.
| Feature Name | Description | Benefits |
|---|---|---|
| Remote Access and Control | Enables administrators to connect to and manage remote computers securely. | Troubleshooting, software installation, configuration changes, and remote support. |
| Real-Time Monitoring | Allows administrators to observe ongoing activities on remote computers. | Identify performance bottlenecks, security threats, and user errors in real time. |
| Activity Logging and Reporting | Provides detailed records of user actions, system events, and application usage. | Identify trends, assess productivity, and investigate security incidents. |
| Screen Recording | Captures the visual activity on a remote computer. | Training, performance reviews, and security investigations. |
| Keystroke Monitoring | Captures every keystroke entered on a remote computer. | Monitor employee productivity, identify security risks, and prevent data leaks. |
| User Activity Tracking | Monitors user actions on remote computers. | Assess employee productivity, identify potential security threats, and improve user experience. |
| Alerting and Notifications | Informs administrators of critical events. | Enable timely intervention and minimize downtime. |
| Data Security and Compliance | Enhances data security and compliance. | Ensure data confidentiality and integrity. |
| Remote Device Management | Allows administrators to manage and configure remote computers. | Simplify device management and ensure consistent security across the network. |
| User Management and Permissions | Controls access to remote computers and specific resources. | Ensure that only authorized users can access sensitive information and applications. |
| Reporting and Analytics | Provides comprehensive insights into user activity, system performance, and security threats. | Identify trends, assess productivity, and make informed decisions. |
| Integration with Other Systems | Integrates with other systems, such as ticketing systems, identity management platforms, and security information and event management (SIEM) tools. | Streamline workflows and provide a unified view of security and performance data. |
Benefits of Using Remote Desktop Monitoring Software
Remote desktop monitoring software offers a range of advantages for businesses and organizations, enabling them to optimize productivity, enhance security, and ensure compliance. By providing valuable insights into employee activities and system behavior, this software empowers organizations to make informed decisions and address potential risks proactively.
Improved Productivity
Remote desktop monitoring software plays a crucial role in boosting employee productivity by offering visibility into their work patterns and identifying areas for improvement.
- Real-time Activity Tracking: By monitoring employee activity in real-time, organizations can identify time-consuming tasks, inefficient workflows, and potential distractions. This data enables managers to provide targeted support and guidance, optimizing employee performance.
- Performance Analysis: The software can generate detailed reports on employee productivity, including keystrokes, mouse clicks, and application usage. These insights allow managers to identify areas where employees may need additional training or resources, leading to improved efficiency and effectiveness.
- Time Management: Remote desktop monitoring software can help employees manage their time more effectively. By tracking time spent on specific tasks, employees can identify areas where they are spending too much or too little time, leading to improved time allocation and overall productivity.
Enhanced Security
Remote desktop monitoring software is essential for strengthening cybersecurity measures and mitigating potential risks.
- Threat Detection: The software can monitor for suspicious activity, such as unauthorized access attempts, malware infections, or data breaches. By identifying these threats early, organizations can take immediate action to prevent data loss and system compromise.
- Data Loss Prevention: Remote desktop monitoring software can help prevent data loss by monitoring sensitive information access and transfer. By setting alerts for unauthorized access or data transfer attempts, organizations can protect their valuable data from unauthorized access or misuse.
- Compliance Monitoring: In industries with strict regulatory requirements, such as healthcare or finance, remote desktop monitoring software can help organizations comply with data privacy and security regulations. By tracking user activity and ensuring compliance with industry standards, organizations can mitigate the risk of fines or penalties.
Improved Compliance
Remote desktop monitoring software can help organizations meet regulatory requirements and maintain compliance with industry standards.
- Audit Trail: The software provides a detailed audit trail of all user activity, including logins, logout, file access, and application usage. This audit trail serves as evidence of compliance and can be used to demonstrate adherence to regulatory requirements.
- Policy Enforcement: Remote desktop monitoring software can be configured to enforce company policies, such as password complexity requirements, data encryption, and access control measures. This ensures that employees adhere to company standards and reduces the risk of non-compliance.
- Risk Mitigation: By identifying and addressing potential compliance risks early, remote desktop monitoring software can help organizations avoid costly fines or penalties. The software provides insights into user behavior and system activity, enabling organizations to proactively address potential compliance issues.
Types of Remote Desktop Monitoring Software
Remote desktop monitoring software comes in various forms, each tailored to specific needs and audiences. Understanding the different types available is crucial for selecting the right solution for your organization.
Types of Remote Desktop Monitoring Software
There are three main types of remote desktop monitoring software:
- Basic Remote Desktop Monitoring Software: This type is designed for simple monitoring and control of remote computers. It typically offers features like screen viewing, remote control, and basic activity logging. Basic software is often free or available at a low cost, making it suitable for small businesses and individuals who need occasional remote access.
- Advanced Remote Desktop Monitoring Software: This type goes beyond basic monitoring and offers a wider range of features, including detailed activity logging, keystroke monitoring, website and application blocking, and user management. Advanced software is often used by organizations with larger workforces, where comprehensive monitoring and control are essential for security and productivity.
- Specialized Remote Desktop Monitoring Software: This type focuses on specific use cases, such as employee monitoring, IT support, or cybersecurity. Specialized software often integrates with other systems, offers advanced reporting and analytics, and may be tailored to industry-specific needs.
Key Features of Different Types of Remote Desktop Monitoring Software
| Type | Key Features | Suitable Use Cases |
|---|---|---|
| Basic Remote Desktop Monitoring Software | Screen viewing, remote control, basic activity logging | Small businesses, individuals needing occasional remote access |
| Advanced Remote Desktop Monitoring Software | Detailed activity logging, keystroke monitoring, website and application blocking, user management | Organizations with larger workforces, where comprehensive monitoring and control are essential for security and productivity |
| Specialized Remote Desktop Monitoring Software | Industry-specific features, advanced reporting and analytics, integration with other systems | Employee monitoring, IT support, cybersecurity |
Pricing Models for Different Types of Remote Desktop Monitoring Software
The pricing models for remote desktop monitoring software vary depending on the type and features offered. Some common models include:
- Subscription-based: This model involves paying a recurring monthly or annual fee for access to the software. It is often the most common pricing model for advanced and specialized software.
- Per-user: This model charges a fee for each user being monitored. It is commonly used by software that focuses on employee monitoring.
- Per-device: This model charges a fee for each device being monitored. It is often used by software that focuses on IT support and cybersecurity.
- Free trial: Many software providers offer free trials to allow potential users to evaluate the software before committing to a purchase.
Choosing the Right Remote Desktop Monitoring Software
Selecting the ideal remote desktop monitoring software requires careful consideration of various factors to ensure it aligns with your specific business needs and requirements. This decision is crucial as it directly impacts the efficiency and security of your remote workforce.
Factors to Consider When Selecting Remote Desktop Monitoring Software
Choosing the right remote desktop monitoring software involves evaluating several key factors to ensure a solution that meets your specific needs and requirements.
- Scalability: As your business grows, your remote desktop monitoring software should be able to scale with your needs. Look for solutions that offer flexible pricing models and can accommodate increasing numbers of users and devices.
- Features: Remote desktop monitoring software comes with a variety of features. Identify the features that are most important to your business. For example, if you need to monitor employee activity, you’ll need software with features such as keystroke logging, screen recording, and website blocking.
- Security: Security is paramount when choosing remote desktop monitoring software. Look for solutions that offer strong encryption, two-factor authentication, and other security features to protect your data.
- Ease of Use: The software should be easy to use for both administrators and end users. Look for solutions with intuitive interfaces and comprehensive documentation.
- Support: Ensure that the software provider offers reliable customer support. This is especially important if you have any technical issues or need help with the software.
- Price: Remote desktop monitoring software comes at different price points. Choose a solution that fits your budget and offers the features you need.
Checklist for Evaluating Different Software Solutions
A checklist helps ensure a comprehensive evaluation of different software solutions. It provides a structured framework to compare features, functionalities, and pricing, aiding in making an informed decision.
- Feature Comparison: Analyze the core features of each software solution. Consider features such as real-time monitoring, screen recording, keystroke logging, website blocking, remote control, and reporting capabilities.
- Security Measures: Evaluate the security features of each solution. Look for strong encryption, two-factor authentication, access controls, and regular security updates.
- User Interface and Usability: Assess the user interface and ease of use for both administrators and end users. Consider factors such as intuitive navigation, clear instructions, and comprehensive documentation.
- Integration Capabilities: Determine the software’s integration capabilities with other business systems. Consider integrations with your existing IT infrastructure, communication tools, and reporting platforms.
- Customer Support: Evaluate the level of customer support provided by each software vendor. Consider factors such as response time, availability, and communication channels.
- Pricing and Value: Compare the pricing models and value offered by each software solution. Consider factors such as subscription fees, feature packages, and support options.
Aligning Software Selection with Business Needs and Requirements
Aligning the software selection with specific business needs and requirements is essential for maximizing its effectiveness. This involves understanding the unique challenges and goals of your organization and choosing a solution that addresses them directly.
“The right remote desktop monitoring software should not only enhance productivity but also ensure the security and compliance of your remote workforce.”
Implementation and Deployment
Implementing and deploying remote desktop monitoring software involves a methodical approach to ensure seamless integration and user adoption. The process encompasses various stages, including configuration, user training, and integration with existing systems.
Configuration
Configuration is the cornerstone of successful deployment. It involves tailoring the software to meet specific organizational needs and security protocols.
- Define Monitoring Policies: Establish clear monitoring policies outlining the scope, frequency, and type of data to be collected. This includes specifying which users, applications, and activities are to be monitored.
- Configure User Access and Permissions: Determine which users have access to the monitoring software and define their permissions. This ensures that only authorized personnel can view and analyze the collected data.
- Set Up Alerts and Notifications: Configure alerts and notifications to trigger when specific events occur, such as unauthorized access attempts, suspicious activity, or system performance issues.
- Integrate with Existing Systems: Integrate the monitoring software with existing systems like Active Directory, SIEM, or ticketing systems to streamline data analysis and incident response.
User Training, Remote desktop monitoring software
Effective user training is crucial to ensure users understand the purpose and functionality of the monitoring software.
- Provide Comprehensive Training Materials: Develop training materials that cover the software’s features, functionalities, and best practices for using the software effectively.
- Conduct Interactive Training Sessions: Conduct interactive training sessions to provide hands-on experience and address user queries. This helps users become familiar with the software and its capabilities.
- Offer Ongoing Support: Provide ongoing support to users through documentation, FAQs, and dedicated support channels to address any issues or concerns.
Integration with Existing Systems
Integrating remote desktop monitoring software with existing systems enhances efficiency and streamlines data analysis.
- Active Directory Integration: Integrate with Active Directory to automate user provisioning and access control, ensuring only authorized users can access the monitoring software.
- SIEM Integration: Integrate with Security Information and Event Management (SIEM) systems to centralize security data and analyze potential threats.
- Ticketing System Integration: Integrate with ticketing systems to automatically create incident tickets based on detected events, facilitating efficient incident response.
Step-by-Step Deployment Guide
- Needs Assessment: Identify the specific monitoring requirements and define the scope of the deployment.
- Software Selection: Choose a remote desktop monitoring software that aligns with the identified requirements and budget.
- Configuration: Configure the software according to the established monitoring policies, user permissions, and alert settings.
- User Training: Provide comprehensive training materials and conduct interactive sessions to familiarize users with the software.
- System Integration: Integrate the software with existing systems like Active Directory, SIEM, and ticketing systems.
- Pilot Testing: Conduct pilot testing to evaluate the software’s performance and identify any potential issues.
- Deployment: Roll out the software to the target user base after successful pilot testing.
- Monitoring and Optimization: Continuously monitor the software’s performance and make necessary adjustments to optimize its effectiveness.
Best Practices for Using Remote Desktop Monitoring Software
Remote desktop monitoring software can be a valuable tool for businesses to enhance productivity, security, and compliance. However, it’s crucial to use this technology responsibly and ethically. This section Artikels best practices for maximizing the benefits of remote desktop monitoring while minimizing potential risks.
Optimizing Software Features
Optimizing remote desktop monitoring software involves configuring its features to achieve the desired balance between monitoring and employee privacy. Here are some key considerations:
- Clearly Define Monitoring Scope: Determine specific activities to be monitored, such as website access, application usage, or keystrokes. This ensures that monitoring is focused and avoids unnecessary intrusion into employee privacy.
- Set Realistic Expectations: Understand that monitoring can’t prevent all security threats or ensure 100% productivity. Use it as a tool to identify potential issues and address them proactively.
- Configure Alerts and Notifications: Establish clear thresholds and triggers for alerts based on predefined criteria. This helps prioritize critical events and avoid overwhelming employees with unnecessary notifications.
- Regularly Review and Update Settings: As business needs evolve, revisit monitoring policies and software configurations to ensure they remain aligned with current requirements and industry best practices.
Data Privacy and Security
Data privacy is paramount when using remote desktop monitoring software. It’s essential to implement measures to protect sensitive employee information and comply with relevant regulations:
- Data Encryption: Employ strong encryption protocols for all data transmitted and stored, including keystrokes, screenshots, and other sensitive information. This ensures data confidentiality and protects it from unauthorized access.
- Access Control: Limit access to monitoring data to authorized personnel with legitimate business needs. Implement robust authentication and authorization mechanisms to prevent unauthorized access.
- Data Retention Policies: Establish clear data retention policies, specifying the duration for which monitoring data is stored and how it is disposed of. This helps balance monitoring needs with data privacy considerations.
- Regular Security Audits: Conduct periodic security audits to identify and address vulnerabilities in the monitoring software and infrastructure. This helps ensure the integrity and confidentiality of monitored data.
Ethical Considerations and Legal Implications
Employee monitoring raises ethical concerns and legal implications. It’s crucial to be transparent with employees about monitoring practices and comply with relevant laws and regulations:
- Transparency and Consent: Inform employees about monitoring practices, including the types of data collected, the purpose of monitoring, and their rights regarding data access and privacy. Obtain informed consent from employees before implementing monitoring.
- Respect for Privacy: Avoid monitoring private communications, such as personal emails or instant messages, unless there is a legitimate business reason and legal justification. Focus on work-related activities and minimize intrusion into employees’ personal lives.
- Compliance with Laws and Regulations: Stay informed about applicable laws and regulations regarding employee monitoring, such as the Electronic Communications Privacy Act (ECPA) in the United States. Ensure compliance with these regulations to avoid legal penalties.
- Employee Training: Provide employees with training on monitoring policies, data privacy, and their rights. This helps foster a culture of transparency and understanding regarding monitoring practices.
Security Considerations
Remote desktop monitoring software, while offering significant benefits for businesses, also introduces potential security risks that must be addressed. Failure to implement robust security measures can lead to data breaches, unauthorized access, and other security vulnerabilities.
Data Encryption
Data encryption is crucial for safeguarding sensitive information transmitted between the monitored devices and the monitoring server. Encryption algorithms like AES-256, commonly used for its high level of security, transform data into an unreadable format, making it incomprehensible to unauthorized individuals. This ensures that even if data is intercepted during transmission, it remains protected.
Encryption is essential to protect data confidentiality and integrity.
Access Control
Implementing robust access control measures is critical to restrict unauthorized access to the monitoring system. This involves:
- Strong Authentication: Using multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification, such as passwords and one-time codes. This makes it significantly harder for unauthorized individuals to gain access.
- Role-Based Access Control (RBAC): RBAC assigns specific permissions to users based on their roles within the organization. This ensures that only authorized individuals have access to the information they need to perform their duties.
- Least Privilege Principle: Users should only be granted the minimum level of access required for their tasks. This minimizes the potential damage that could result from unauthorized access.
Regular Security Audits
Regular security audits are essential to identify and address vulnerabilities in the monitoring system. These audits should be conducted by qualified security professionals who can assess the system’s security posture, identify potential weaknesses, and recommend appropriate mitigation strategies.
Regular security audits are crucial to ensure that the monitoring system remains secure.
Outcome Summary
In conclusion, remote desktop monitoring software offers a multifaceted solution for businesses seeking to enhance productivity, security, and compliance. By providing real-time insights into employee activities, this technology empowers organizations to optimize operations, mitigate risks, and foster a more productive and secure work environment. As technology continues to evolve, remote desktop monitoring software is poised to play an increasingly vital role in the future of work, enabling businesses to navigate the complexities of the digital landscape with greater confidence and efficiency.
Remote desktop monitoring software can be a valuable tool for IT professionals, allowing them to troubleshoot issues and manage systems remotely. For optimal performance, it’s essential to ensure that all necessary drivers are installed, including lenovo drivers for Lenovo devices.
This ensures that the software can properly interact with the hardware and provide the most accurate and efficient monitoring experience.