RAR Password Unlocker: Ever stumbled upon a RAR archive with a password you’ve forgotten? Or perhaps you need to access a file locked away behind a cryptic combination? This is where RAR password unlockers come into play, offering a potential solution to unlock the secrets within those encrypted archives. But before diving into the world of password cracking, it’s crucial to understand the complexities, ethical considerations, and potential risks involved.
Table of Contents
RAR files are a common format for compressing and archiving data, often used to share large files or protect sensitive information. Password protection adds an extra layer of security, ensuring only authorized individuals can access the contents. While this is beneficial in many situations, it can also lead to situations where access is lost or forgotten. This is where the need for RAR password unlockers arises.
The Need for RAR Password Unlockers
RAR password unlockers are software tools designed to recover lost or forgotten passwords for RAR archives. While the primary function is to help users regain access to their data, these tools have legitimate uses and ethical considerations surrounding their application.
Legitimate Uses
RAR password unlockers can be valuable in various situations where a user needs to access a RAR archive but has forgotten the password. Here are some examples of legitimate uses:
- Forgotten Password: A user might have forgotten the password for an important RAR archive containing personal documents, financial records, or work files. A password unlocker can help them recover the password and access their data.
- Password Recovery After System Failure: A user might have lost access to their computer due to a system failure, and their important data is stored in a RAR archive. A password unlocker can help them retrieve the password and access their files.
- Access to Legacy Archives: A user might have inherited a RAR archive from a deceased relative or friend, and they need to access the contents. A password unlocker can help them unlock the archive and access the data.
Ethical Considerations
While RAR password unlockers can be useful for legitimate purposes, they also raise ethical concerns. It is crucial to use these tools responsibly and ethically.
- Privacy Concerns: Password unlockers can be used to access sensitive information stored in RAR archives, raising concerns about privacy and data security. It is essential to use these tools only when you have a legitimate right to access the data.
- Legal Implications: In some jurisdictions, using password unlockers to access data without authorization may be illegal. It is crucial to understand the legal implications of using these tools in your specific location.
- Respect for Others: It is unethical to use password unlockers to access someone else’s data without their permission. This includes using them to access personal files, emails, or other private information.
Types of RAR Password Unlockers
RAR password unlockers employ various techniques to recover lost or forgotten passwords. Understanding these methods is crucial for choosing the right tool and assessing its effectiveness.
Brute Force Attacks
Brute force attacks are the most straightforward method. They involve systematically trying every possible combination of characters until the correct password is found.
- Pros: Brute force attacks are guaranteed to find the password eventually, provided enough time and resources are available.
- Cons: The time required for a brute force attack can be extremely long, especially for complex passwords. This method is computationally intensive and may not be practical for longer passwords or those with a large character set.
For example, a password consisting of 8 lowercase letters would require trying 268 (approximately 208 billion) combinations. This would take an exceptionally long time, even with powerful computers.
Dictionary Attacks
Dictionary attacks utilize a list of common passwords or word combinations. They try these pre-defined passwords against the encrypted RAR archive.
- Pros: Dictionary attacks are significantly faster than brute force attacks, especially if the password is common or follows a predictable pattern.
- Cons: Dictionary attacks are only effective if the password is in the dictionary. They may not be successful if the password is unique or complex.
Many password lists are available online, containing common passwords, names, dates, and other frequently used phrases.
Hybrid Attacks
Hybrid attacks combine elements of both brute force and dictionary attacks. They start by trying common passwords from a dictionary and then switch to brute force if the dictionary attack fails.
- Pros: Hybrid attacks offer a good balance between speed and effectiveness. They can quickly try common passwords and then switch to brute force to find more complex passwords.
- Cons: Hybrid attacks are more complex to implement than simple brute force or dictionary attacks.
Mask Attacks
Mask attacks use a pattern to narrow down the possible password combinations. This pattern can include character types, length, and other constraints.
- Pros: Mask attacks can significantly reduce the search space for the password, making the process faster and more efficient.
- Cons: Mask attacks require knowledge about the password structure. If the pattern is incorrect, the attack will be ineffective.
For example, a mask could be defined as “?l?l?l?l?l?l” indicating a password with eight lowercase letters. This would significantly reduce the search space compared to a brute force attack.
Rainbow Tables
Rainbow tables are pre-computed tables containing password hashes and their corresponding plain-text passwords. They are used to quickly find the password by comparing the hash of the encrypted archive to the table.
- Pros: Rainbow tables are extremely fast and can recover passwords almost instantly.
- Cons: Rainbow tables are large and require significant storage space. They are also less effective against strong passwords with unique character combinations.
Other Methods, Rar password unlocker
In addition to the above methods, some password unlockers employ advanced techniques such as:
- GPU acceleration: This method utilizes the processing power of graphics cards to accelerate the password cracking process.
- Cloud computing: This approach distributes the password cracking workload across multiple computers in the cloud, further speeding up the process.
Popular RAR Password Unlocker Tools
When choosing a RAR password unlocker, you need to consider several factors, including the features offered, compatibility with your operating system, pricing, and user reviews. Here are some popular RAR password unlocker tools that you can consider.
Popular RAR Password Unlocker Tools
There are many different RAR password unlocker tools available, each with its own strengths and weaknesses. Here is a comparison of some of the most popular tools.
If you’re trying to unlock a RAR file, you’ll need a specialized password recovery tool. While those can be helpful, sometimes it’s easier to just ask for the password. If you’re working remotely with someone who has the password, you might consider using a remote desktop tool like anydesk download free to access their computer directly.
Once you’re in, they can easily provide the password to the RAR file, and you can get to work.
| Tool | Features | Compatibility | Pricing | User Reviews |
|---|---|---|---|---|
| RAR Password Unlocker | Brute-force attack, dictionary attack, mask attack | Windows | $29.95 | 4.5/5 stars |
| Advanced RAR Password Recovery | Brute-force attack, dictionary attack, mask attack, GPU acceleration | Windows | $49.95 | 4.2/5 stars |
| Passware Kit Forensic | Brute-force attack, dictionary attack, mask attack, GPU acceleration, support for various file formats | Windows, macOS, Linux | $995 | 4.8/5 stars |
| Elcomsoft Advanced Archive Password Recovery | Brute-force attack, dictionary attack, mask attack, GPU acceleration, support for various archive formats | Windows, macOS | $199 | 4.6/5 stars |
Using RAR Password Unlockers
Using RAR password unlockers is a straightforward process, but it requires patience, as it can take time to crack a complex password. This section will guide you through the process of using a chosen RAR password unlocker.
Setting Up and Configuring a RAR Password Unlocker
Once you’ve chosen a RAR password unlocker, you need to set it up and configure it to work with your specific needs. Here’s a step-by-step guide on how to do this:
- Download and Install: Download the RAR password unlocker software from the official website. Ensure you download it from a trusted source to avoid malware. Once downloaded, install the software on your computer following the on-screen instructions.
- Open the Software: After installation, launch the RAR password unlocker software. The interface may vary depending on the software you choose, but most have a similar layout.
- Add the RAR Archive: Locate the encrypted RAR archive you want to unlock. You can do this by browsing your computer or dragging and dropping the file directly into the software’s window.
- Choose Attack Type: Select the type of attack you want to use to crack the password. There are different attack types, including brute force, dictionary attack, and mask attack. The choice depends on the complexity of the password and the resources you have available.
- Configure Settings: Depending on the attack type, you might need to configure some settings. For example, you might need to specify a character set, password length, or dictionary file to use for the attack.
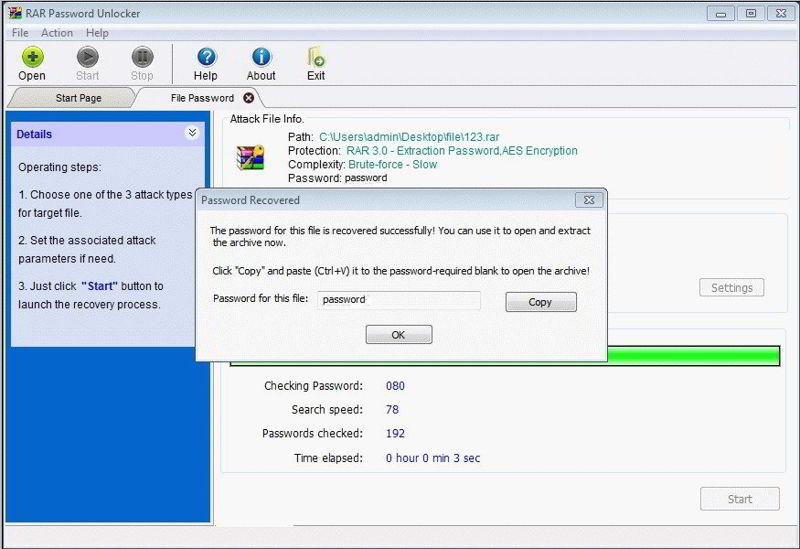
- Start the Attack: Once you’ve set up the attack, start the process by clicking the “Start” or “Crack” button. The software will start trying different password combinations to unlock the archive.
Alternatives to RAR Password Unlockers
Sometimes, brute-forcing your way into a RAR file isn’t the most efficient or even possible solution. There are alternative methods that might be worth considering, offering different approaches to retrieving the password.
These methods offer different strengths and weaknesses compared to traditional password unlockers, and understanding them is crucial for choosing the right approach for your situation.
Password Managers
Password managers are software applications that securely store and manage your passwords, offering an alternative to brute-forcing RAR files. If you’ve forgotten the password to a RAR file, and you’ve previously saved it within a password manager, retrieving it might be simpler than resorting to password unlockers.
Password managers often have features like:
- Strong Password Generation: They can generate strong and unique passwords, improving your overall security posture.
- Password Storage: They securely store your passwords, eliminating the need to remember them all.
- Autofill: They automatically fill in login credentials, making browsing more convenient.
- Password Synchronization: They allow you to synchronize your passwords across multiple devices, ensuring access from anywhere.
Important Note: While password managers are excellent for password management, they are only helpful if you’ve already stored the RAR file password within them.
Future of RAR Password Security: Rar Password Unlocker
The realm of password security is in a constant state of evolution, with advancements in encryption techniques and the emergence of new threats. This dynamic landscape influences the future of RAR password protection and the effectiveness of unlockers.
RAR Password Protection Advancements
The future of RAR password protection likely involves the implementation of more robust encryption algorithms and enhanced security features. These advancements aim to make it increasingly difficult for unauthorized individuals to access protected files.
- Advanced Encryption Standards: The adoption of stronger encryption algorithms, such as AES-256, will significantly increase the complexity of password cracking attempts. This level of encryption is widely considered to be highly secure, making it extremely challenging for even sophisticated attackers to break.
- Salt and Hashing Techniques: Implementing salt and hashing techniques further enhances password security. Salt adds random data to the password before hashing, making it more difficult for attackers to use pre-computed tables to crack passwords.
- Multi-Factor Authentication: Integrating multi-factor authentication (MFA) into RAR password protection could provide an extra layer of security. This would require users to provide multiple forms of identification, such as a password and a unique code from a mobile device, before accessing protected files.
Evolving Landscape of Password Security
The evolving landscape of password security is characterized by a growing awareness of the vulnerabilities associated with traditional password-based authentication. This awareness has led to the adoption of alternative authentication methods and the development of more sophisticated security protocols.
- Passwordless Authentication: Passwordless authentication methods, such as biometrics (fingerprint scanning, facial recognition) and security keys, are gaining traction as they eliminate the need for users to remember complex passwords. These methods are generally considered more secure as they rely on unique physical or biological characteristics.
- Zero-Trust Security: Zero-trust security models assume that no user or device can be trusted by default. This approach emphasizes strict verification and authorization procedures, requiring users to constantly prove their identity and access privileges before accessing sensitive information.
- Artificial Intelligence and Machine Learning: AI and ML technologies are being used to detect and prevent password attacks. These systems can analyze patterns in user behavior and identify suspicious activities, helping to mitigate the risk of unauthorized access.
Future of RAR Password Unlockers
The future of RAR password unlockers is likely to be influenced by the advancements in password security and the evolving threat landscape.
- Increased Complexity: As encryption algorithms become more sophisticated and security features are enhanced, password unlockers will need to adapt to overcome these challenges. This may require the development of more advanced cracking techniques and the use of specialized hardware to accelerate the process.
- Limited Effectiveness: With the adoption of stronger encryption standards and multi-factor authentication, the effectiveness of brute-force attacks and dictionary-based methods will be significantly reduced. This means that password unlockers may become less reliable in cracking passwords, particularly for highly secure archives.
- Ethical Considerations: The use of password unlockers raises ethical concerns, particularly when used for unauthorized access. As password security strengthens, the ethical implications of using password unlockers will become more prominent.
Conclusion
Navigating the world of RAR password unlockers requires a balance of understanding and caution. While they offer a potential solution for recovering access to locked archives, it’s essential to use them responsibly and ethically. Remember that unauthorized access to encrypted data can have serious legal consequences. Ultimately, the best approach is to prioritize strong password practices, utilize secure password managers, and explore alternative methods for recovering access before resorting to password unlockers. By understanding the intricacies of RAR password security and employing responsible practices, you can navigate the digital landscape with greater confidence.
