Remote monitoring software has become an indispensable tool for businesses of all sizes, offering a comprehensive view of their systems and applications, no matter where they are located. It empowers organizations to proactively manage their infrastructure, identify potential issues before they escalate, and optimize performance for maximum efficiency.
Table of Contents
This software leverages advanced technology to collect, analyze, and present data in real-time, providing actionable insights that help businesses make informed decisions. From network monitoring to server performance and application health, remote monitoring software encompasses a wide range of functionalities, each designed to enhance operational efficiency, security, and overall success.
Introduction to Remote Monitoring Software
Remote monitoring software is a powerful tool that allows businesses to keep a watchful eye on their operations, systems, and assets from any location. It provides real-time insights and data, enabling proactive maintenance, early problem detection, and improved efficiency.
Remote monitoring software collects and analyzes data from various sources, such as sensors, devices, and applications, to provide comprehensive visibility into critical aspects of an organization. This data can be visualized through dashboards, reports, and alerts, allowing users to identify trends, anomalies, and potential issues before they escalate.
Benefits of Remote Monitoring Software
The benefits of using remote monitoring software are numerous and can significantly impact an organization’s success. These benefits include:
- Enhanced Visibility and Control: Remote monitoring software provides a centralized platform for monitoring multiple systems and devices, offering a comprehensive overview of operations. This enhanced visibility empowers businesses to make informed decisions based on real-time data.
- Proactive Maintenance and Issue Resolution: By identifying potential issues early, remote monitoring software enables proactive maintenance and troubleshooting. This reduces downtime, minimizes disruptions, and optimizes system performance.
- Improved Efficiency and Productivity: Remote monitoring software streamlines operations by automating tasks, reducing manual intervention, and providing insights that lead to process optimization. This can significantly improve efficiency and productivity across various departments.
- Cost Savings: Remote monitoring software can help organizations save costs by reducing downtime, preventing equipment failures, and optimizing resource utilization. It also minimizes the need for on-site visits, further reducing expenses.
- Increased Security: Remote monitoring software can play a crucial role in enhancing security by detecting and responding to security threats in real-time. It can monitor network traffic, identify suspicious activities, and trigger alerts to security teams, enabling swift and effective response.
Real-World Examples of Remote Monitoring Software Use
Remote monitoring software finds applications across various industries, enabling organizations to optimize their operations and improve efficiency. Here are some real-world examples:
- Healthcare: Hospitals use remote monitoring software to track patient vitals, medication administration, and equipment performance. This enables proactive care, reduces medical errors, and improves patient outcomes.
- Manufacturing: Manufacturing plants leverage remote monitoring software to monitor production lines, equipment performance, and environmental conditions. This ensures optimal production, minimizes downtime, and improves product quality.
- Data Centers: Data centers rely on remote monitoring software to monitor server performance, network traffic, and environmental conditions. This ensures data center stability, prevents outages, and maintains optimal performance.
- Retail: Retailers use remote monitoring software to track inventory levels, customer behavior, and store performance. This helps optimize inventory management, improve customer experience, and enhance store efficiency.
- Energy and Utilities: Energy companies utilize remote monitoring software to monitor power grids, pipelines, and renewable energy sources. This enables efficient energy distribution, reduces energy waste, and improves reliability.
Types of Remote Monitoring Software
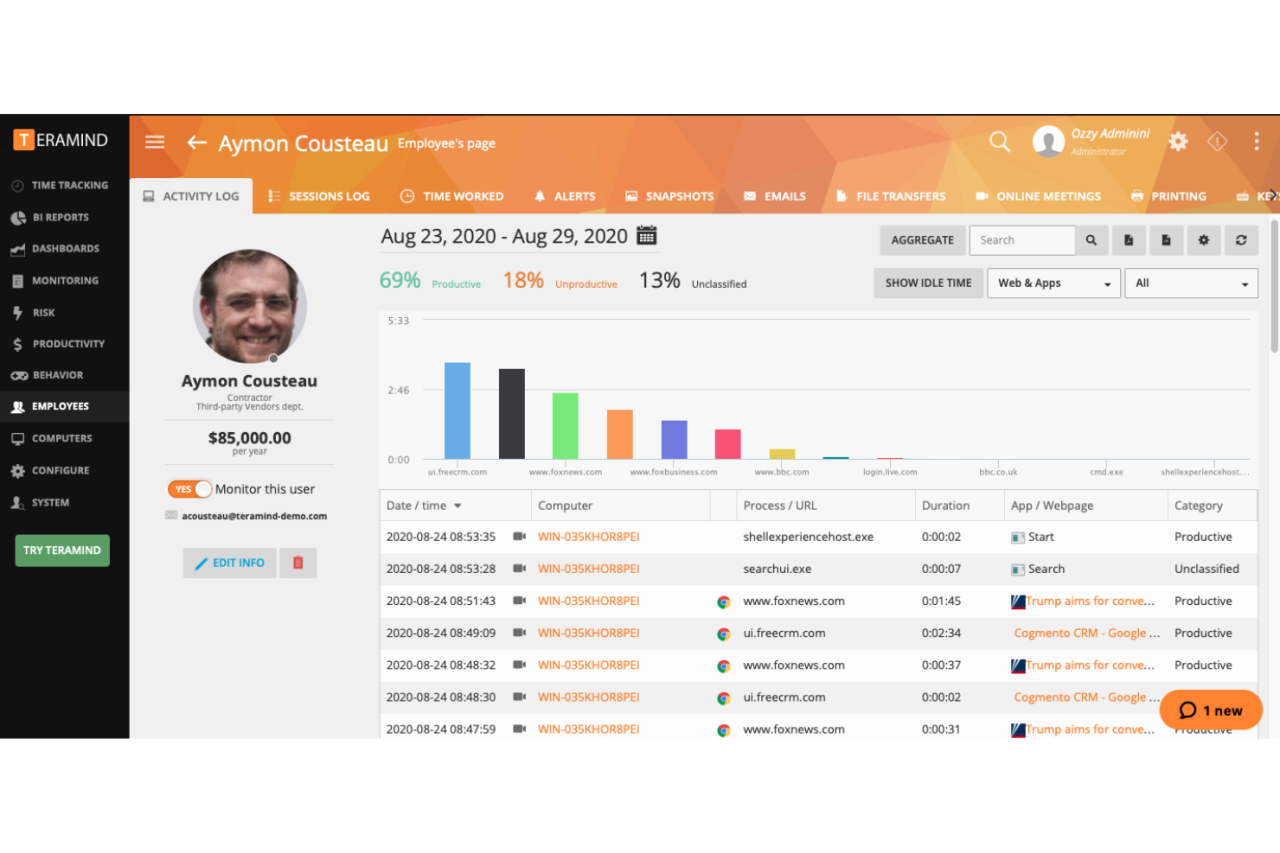
Remote monitoring software comes in various forms, each tailored to specific monitoring needs. Understanding the different types can help you choose the right solution for your organization.
Network Monitoring
Network monitoring software plays a crucial role in ensuring the smooth operation of your network infrastructure. It provides real-time insights into network performance, identifying potential bottlenecks and security threats. Key features include:
- Traffic Analysis: Monitoring network traffic patterns to identify anomalies, bandwidth usage trends, and potential security risks.
- Performance Monitoring: Tracking network latency, packet loss, and other metrics to identify performance issues and optimize network performance.
- Security Monitoring: Detecting suspicious activity, intrusion attempts, and malware infections to safeguard your network.
- Alerting and Reporting: Generating alerts for critical events and providing detailed reports on network performance and security.
Popular examples of network monitoring software include:
- SolarWinds Network Performance Monitor: Comprehensive network monitoring solution with advanced features for traffic analysis, performance optimization, and security.
- PRTG Network Monitor: User-friendly network monitoring software with a wide range of sensors for monitoring various network devices and services.
- ManageEngine OpManager: Enterprise-grade network monitoring software with robust capabilities for network performance, security, and availability management.
Server Monitoring
Server monitoring software is essential for maintaining the uptime and performance of your servers. It provides continuous monitoring of server resources, health, and performance, enabling proactive issue resolution. Key features include:
- Resource Monitoring: Tracking CPU utilization, memory usage, disk space, and other server resources to identify potential performance bottlenecks.
- Health Monitoring: Checking server health status, including temperature, fan speed, and power supply, to prevent hardware failures.
- Performance Monitoring: Analyzing server response times, throughput, and other metrics to ensure optimal performance.
- Security Monitoring: Detecting security vulnerabilities, unauthorized access attempts, and malware infections.
- Alerting and Reporting: Generating alerts for critical events and providing detailed reports on server performance and health.
Popular examples of server monitoring software include:
- Datadog: Cloud-based monitoring platform offering comprehensive server monitoring, along with other features like application performance monitoring and infrastructure monitoring.
- New Relic: Application performance monitoring platform that also provides server monitoring capabilities, focusing on application performance and user experience.
- Nagios: Open-source server monitoring software known for its flexibility and extensibility, enabling customization for specific monitoring needs.
Application Performance Monitoring (APM)
Application performance monitoring (APM) software focuses on monitoring the performance and health of applications, providing insights into user experience, code performance, and infrastructure issues. Key features include:
- Transaction Monitoring: Tracking the performance of individual user transactions to identify bottlenecks and slowdowns.
- Code Profiling: Analyzing application code to identify performance issues and optimize code efficiency.
- Error Tracking: Identifying and analyzing application errors to diagnose and resolve issues quickly.
- User Experience Monitoring: Tracking user interactions and response times to understand the impact of performance issues on user experience.
- Alerting and Reporting: Generating alerts for critical events and providing detailed reports on application performance and health.
Popular examples of APM software include:
- Dynatrace: Comprehensive APM platform offering advanced features for code profiling, error tracking, and user experience monitoring.
- AppDynamics: APM solution focused on application performance optimization and user experience monitoring, with deep insights into application code and infrastructure.
- Splunk: Observability platform that includes APM capabilities, enabling monitoring of applications, infrastructure, and security events.
Key Features of Remote Monitoring Software

Remote monitoring software is designed to provide comprehensive insights into the performance and health of your IT infrastructure. It empowers organizations to proactively identify and address potential issues before they escalate into major disruptions.
Real-Time Data Visualization and Reporting
Real-time data visualization and reporting are crucial for effective remote monitoring. These capabilities allow you to gain a clear understanding of your system’s performance and identify trends that may indicate potential problems.
- Interactive Dashboards: Dashboards provide a centralized view of key performance indicators (KPIs) and system metrics. They allow you to monitor multiple aspects of your infrastructure simultaneously, such as CPU utilization, memory usage, network traffic, and application performance.
- Customizable Reports: Customizable reports allow you to generate tailored reports based on your specific monitoring needs. You can filter data by time period, device, or other criteria to gain insights into specific areas of concern. Reports can be used for trend analysis, capacity planning, and performance optimization.
- Historical Data Analysis: Access to historical data allows you to identify patterns and trends over time. This information can be used to predict future performance, optimize resource allocation, and prevent potential issues before they arise. For example, by analyzing historical network traffic data, you can identify peak usage times and adjust network capacity accordingly.
Alerts and Notifications
Alerts and notifications play a vital role in proactive problem management. They alert you to potential issues in real time, enabling you to take corrective action before they impact your operations.
- Threshold-Based Alerts: Threshold-based alerts are triggered when a specific metric exceeds a predefined threshold. For example, you can set an alert for CPU utilization exceeding 80%, or for disk space falling below 10%. This ensures that you are notified of potential issues before they become critical.
- Customizable Alert Rules: Customizable alert rules allow you to tailor alerts to your specific needs. You can define different alert levels based on severity, trigger alerts based on specific events, and configure notification methods to suit your preferences. For example, you can set up critical alerts for system failures that require immediate attention, and informational alerts for routine maintenance tasks.
- Multiple Notification Channels: Remote monitoring software typically supports multiple notification channels, such as email, SMS, and desktop notifications. This ensures that you receive alerts regardless of your location or device. For example, you can receive email alerts for low disk space, SMS alerts for critical system failures, and desktop notifications for routine maintenance tasks.
Benefits of Implementing Remote Monitoring Software
Remote monitoring software offers a range of benefits that can significantly improve operational efficiency, reduce costs, and enhance security. By leveraging real-time data and automated processes, organizations can gain valuable insights into their operations, optimize resource allocation, and proactively address potential issues before they escalate.
Operational Efficiency Gains
Remote monitoring software empowers organizations to streamline their operations and enhance efficiency in various ways.
- Real-time Visibility: Remote monitoring provides a comprehensive and real-time view of critical systems and processes, enabling organizations to identify and address issues promptly. This real-time visibility reduces downtime, minimizes disruptions, and allows for proactive maintenance, ultimately leading to increased productivity and efficiency.
- Automated Processes: Remote monitoring software automates routine tasks, freeing up valuable time for staff to focus on more strategic initiatives. For example, automated alerts for system failures or performance issues can trigger immediate responses, minimizing the impact on operations. This automation streamlines workflows, reduces manual effort, and improves overall efficiency.
- Centralized Management: Remote monitoring software provides a centralized platform for managing multiple systems and devices from a single location. This centralized approach simplifies management, reduces complexity, and enhances visibility across the entire infrastructure, ultimately improving operational efficiency.
Cost Reduction and Resource Optimization
Remote monitoring software plays a crucial role in optimizing resource allocation and reducing operational costs.
- Reduced Downtime: By identifying and addressing issues proactively, remote monitoring software minimizes downtime and associated costs. For example, early detection of system failures or performance bottlenecks can prevent service disruptions and minimize the impact on business operations.
- Optimized Resource Allocation: Remote monitoring provides valuable insights into resource utilization, enabling organizations to optimize resource allocation and reduce waste. For example, by identifying underutilized servers or applications, organizations can consolidate resources, reduce energy consumption, and lower operational costs.
- Improved Maintenance: Remote monitoring software allows for proactive maintenance, reducing the need for reactive repairs and minimizing downtime. By monitoring system health and identifying potential issues before they escalate, organizations can schedule maintenance activities during off-peak hours, minimizing disruption and reducing overall maintenance costs.
Enhanced Security and Compliance
Remote monitoring software enhances security by providing real-time visibility into system activity and detecting potential threats.
- Threat Detection: Remote monitoring software can detect suspicious activity, security breaches, and potential vulnerabilities, enabling organizations to respond quickly and mitigate risks. This proactive approach strengthens security posture and reduces the likelihood of successful attacks.
- Compliance Monitoring: Remote monitoring software can help organizations comply with industry regulations and security standards by providing auditable logs and reports. This ensures that organizations can demonstrate compliance with relevant requirements and minimize the risk of penalties or fines.
- Data Security: Remote monitoring software can help protect sensitive data by detecting and responding to unauthorized access attempts or data breaches. By monitoring system activity and identifying anomalies, organizations can take immediate action to secure data and prevent unauthorized access.
Considerations for Choosing Remote Monitoring Software
Choosing the right remote monitoring software can be a crucial decision for any organization. It’s important to consider various factors that align with your specific needs, budget, and technical capabilities.
Scalability
Scalability is crucial when selecting remote monitoring software, especially for businesses that anticipate growth. It’s essential to choose software that can handle increasing data volumes, devices, and users without compromising performance.
Integration Capabilities
Remote monitoring software should seamlessly integrate with existing systems and tools. This integration ensures data consistency and allows for centralized monitoring and management. Consider factors such as:
- API availability
- Support for various protocols
- Compatibility with existing infrastructure
User-Friendliness
The software should be user-friendly and intuitive, regardless of the technical expertise of the users. This ensures easy adoption, efficient operation, and reduced training requirements.
Pricing Models
Remote monitoring software comes with various pricing models, such as:
- Subscription-based
- Per-device
- Per-feature
It’s important to compare pricing models and choose one that aligns with your budget and usage patterns.
Vendor Support Options
Reliable vendor support is crucial for resolving issues, receiving updates, and ensuring smooth operation. Consider factors such as:
- Response time
- Availability of documentation
- Training and onboarding support
Implementing and Configuring Remote Monitoring Software
The deployment and configuration of remote monitoring software require a systematic approach to ensure effective and secure monitoring. This process involves a series of steps, ranging from initial installation to the fine-tuning of settings for optimal performance.
Steps Involved in Deploying and Configuring Remote Monitoring Software
The deployment and configuration of remote monitoring software involve a series of steps that ensure the software is properly installed, integrated, and optimized for your specific needs. These steps are essential for ensuring the software functions effectively and provides valuable insights into the systems it monitors.
- Software Installation and Configuration: The initial step involves installing the remote monitoring software on the designated server or cloud platform. This typically includes downloading the software package, running the installer, and configuring basic settings such as database connections and user accounts.
- Agent Deployment: Once the software is installed, agents need to be deployed on the devices or systems you want to monitor. These agents collect data and transmit it back to the monitoring software. The deployment process can vary depending on the type of agent (e.g., software agents, hardware agents) and the operating system of the target devices.
- Defining Monitoring Parameters: The next step involves defining the specific parameters you want to monitor. This includes identifying key metrics, such as CPU usage, memory utilization, network traffic, and application performance. You can set up custom dashboards and reports to visualize and analyze these metrics.
- Setting Up Alerts and Thresholds: To ensure timely intervention, you need to configure alerts and thresholds. These alerts trigger notifications when certain metrics exceed predetermined thresholds, indicating potential problems. You can customize alerts based on severity levels and specify the desired notification channels (e.g., email, SMS, push notifications).
- Integration with Existing Systems: Remote monitoring software can be integrated with existing systems, such as ticketing systems, IT service management (ITSM) platforms, and logging systems. This integration allows for automated incident response and streamlined workflows.
- Testing and Optimization: After the initial configuration, it is crucial to test the software thoroughly to ensure it functions correctly and meets your requirements. This includes verifying alert triggers, data accuracy, and the overall performance of the monitoring system.
Best Practices for Setting Up Alerts and Monitoring Thresholds
Setting up alerts and monitoring thresholds effectively is crucial for proactive issue detection and timely resolution. By following best practices, you can optimize your monitoring system to minimize false positives and ensure that alerts are actionable.
- Define Clear Thresholds: When setting up thresholds, it is important to define them based on realistic expectations and historical data. Avoid setting thresholds too low, which can lead to frequent false alarms, or too high, which might miss critical issues.
- Use a Multi-Tiered Approach: Implement a multi-tiered approach to alerts, classifying them by severity levels. For example, you can have critical alerts for severe issues, warning alerts for potential problems, and informational alerts for routine events.
- Consider Time-Based Thresholds: In some cases, it might be beneficial to set up time-based thresholds. For example, you can set a higher threshold for CPU usage during peak hours and a lower threshold during off-peak hours.
- Regularly Review and Adjust: It is important to regularly review and adjust thresholds based on system performance, changes in workload, and evolving requirements.
Guidance on Integrating Remote Monitoring with Existing Systems
Integrating remote monitoring software with existing systems can streamline workflows, automate tasks, and improve overall efficiency. This integration can provide a unified view of your IT infrastructure and enable proactive incident management.
- Ticketing Systems: Integration with ticketing systems allows for automated incident creation and assignment based on triggered alerts. This ensures that issues are promptly addressed and tracked.
- IT Service Management (ITSM) Platforms: Integrating with ITSM platforms enables seamless incident management and workflow automation. Alerts can trigger workflows within the ITSM platform, facilitating incident resolution and tracking.
- Logging Systems: Integration with logging systems allows for centralized log management and analysis. Alerts can trigger the collection and analysis of relevant logs, providing valuable insights into the root cause of issues.
Using Remote Monitoring Software for Proactive Maintenance
Remote monitoring software empowers organizations to transition from reactive to proactive maintenance strategies. By continuously gathering data from systems and devices, this software allows for early detection of potential issues, preventing them from escalating into major disruptions. This approach significantly improves system uptime, reduces downtime costs, and enhances overall operational efficiency.
Data Analysis for Predictive Maintenance
Data analysis plays a crucial role in identifying potential issues before they manifest as problems. By leveraging historical data, real-time metrics, and predictive algorithms, remote monitoring software can identify patterns and anomalies that indicate impending failures. This proactive approach allows for timely intervention, minimizing the impact of potential issues on system performance and availability.
“Predictive maintenance is the ability to anticipate equipment failures and take action before they occur.” – American Society of Mechanical Engineers (ASME)
- Trend Analysis: Analyzing historical data trends, such as increasing temperature, vibration, or power consumption, can indicate potential component wear or malfunctions.
- Anomaly Detection: Identifying unusual deviations from expected performance metrics can flag potential issues, such as unexpected spikes in resource utilization or sudden changes in system behavior.
- Predictive Modeling: Machine learning algorithms can be used to build predictive models based on historical data, allowing for estimations of future system behavior and potential failure points.
Optimizing System Performance and Availability
Proactive maintenance strategies, enabled by remote monitoring software, significantly improve system performance and availability. By addressing potential issues before they cause disruptions, organizations can maintain optimal system operation and minimize downtime.
- Reduced Downtime: Early detection and resolution of potential issues prevent major failures that would otherwise lead to downtime.
- Improved System Efficiency: Proactive maintenance ensures optimal system performance by addressing performance bottlenecks and resource utilization issues before they impact productivity.
- Enhanced User Experience: Proactive maintenance minimizes system disruptions, ensuring a seamless and uninterrupted user experience.
Security Considerations for Remote Monitoring Software
Remote monitoring software provides valuable insights into the health and performance of your systems, but it also introduces security risks. Data security and privacy are paramount concerns when using remote monitoring software, as sensitive information is transmitted and stored remotely.
Robust Authentication and Authorization Mechanisms
Robust authentication and authorization mechanisms are essential for protecting access to your remote monitoring infrastructure.
- Multi-factor authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile app, before granting access. This significantly reduces the risk of unauthorized access, even if a password is compromised.
- Role-based access control (RBAC): RBAC ensures that users have access only to the information and resources they need to perform their duties. This prevents unauthorized access to sensitive data and reduces the potential for security breaches.
- Regular password changes: Enforcing regular password changes helps prevent unauthorized access by users who have forgotten or shared their passwords. This is particularly important for accounts with high-level privileges.
Future Trends in Remote Monitoring Software
The field of remote monitoring software is constantly evolving, driven by advancements in technology and the increasing demand for efficient and proactive management of systems and devices. Emerging technologies like artificial intelligence (AI), machine learning (ML), and cloud computing are shaping the future of remote monitoring, offering enhanced capabilities and new possibilities.
The Role of AI and ML in Remote Monitoring
AI and ML are transforming remote monitoring by enabling more intelligent and automated processes.
- Predictive Maintenance: AI algorithms can analyze historical data and identify patterns that indicate potential equipment failures. This allows for proactive maintenance, reducing downtime and minimizing costs. For example, AI can analyze sensor data from a manufacturing machine to predict when a specific component is likely to fail, allowing for timely replacement before a breakdown occurs.
- Anomaly Detection: ML models can detect unusual patterns in data, alerting administrators to potential security threats or performance issues. These models can identify deviations from normal behavior, flagging suspicious activities that might otherwise go unnoticed.
- Automated Response: AI-powered systems can automate routine tasks, such as restarting servers or adjusting system settings, based on predefined rules and thresholds. This frees up human operators to focus on more complex issues.
Impact of Cloud Computing and Edge Computing
Cloud computing and edge computing are revolutionizing the way remote monitoring solutions are deployed and managed.
- Scalability and Flexibility: Cloud-based platforms offer scalability, allowing businesses to easily adjust their monitoring capabilities as their needs change. They also provide flexibility, enabling access to monitoring data and tools from anywhere with an internet connection.
- Reduced Infrastructure Costs: Cloud solutions eliminate the need for expensive hardware and software investments, reducing upfront costs and ongoing maintenance expenses. Edge computing brings processing power closer to the source of data, reducing latency and improving real-time monitoring capabilities. This is particularly beneficial for applications requiring low latency, such as industrial automation and remote healthcare.
- Enhanced Security: Cloud providers offer robust security measures and compliance certifications, protecting sensitive data and ensuring regulatory compliance. Edge computing can enhance security by processing data locally, reducing the risk of data breaches during transmission.
Integration of IoT and 5G
The Internet of Things (IoT) and 5G technology are further expanding the reach and capabilities of remote monitoring.
- Increased Connectivity: 5G networks provide high-speed, low-latency connectivity, enabling real-time monitoring of a wider range of devices and sensors. This allows for more comprehensive and granular data collection, providing deeper insights into system performance and potential issues.
- Data-Driven Insights: The massive amount of data generated by IoT devices creates opportunities for advanced analytics and insights. Remote monitoring software can leverage this data to optimize operations, improve decision-making, and identify new opportunities for efficiency.
- Remote Control and Automation: 5G and IoT enable remote control and automation of devices and systems, allowing for more efficient management and reduced human intervention. This is particularly relevant in industries such as manufacturing, energy, and transportation, where remote control can improve safety and efficiency.
Case Studies and Success Stories
Remote monitoring software has proven its worth in numerous real-world scenarios, helping organizations across industries optimize operations, enhance efficiency, and achieve tangible business outcomes. Examining these success stories provides valuable insights into the practical applications and benefits of remote monitoring software, offering a glimpse into the real-world impact of this technology.
Benefits Achieved and Challenges Overcome
Successful implementations of remote monitoring software have consistently delivered a range of benefits, including:
- Improved Uptime and Reduced Downtime: By proactively identifying and addressing potential issues before they escalate, remote monitoring software significantly reduces downtime, minimizing disruptions to critical operations and ensuring business continuity. For instance, a large manufacturing company implemented remote monitoring software to track the performance of their production lines. This enabled them to identify and resolve minor issues before they resulted in production stoppages, leading to a 20% reduction in downtime and a 15% increase in production efficiency.
- Enhanced Security and Compliance: Remote monitoring software plays a crucial role in bolstering security by detecting and alerting on potential threats, ensuring compliance with industry regulations, and providing auditable records of system activity. A financial institution implemented remote monitoring software to monitor network traffic and identify suspicious activity, resulting in a 50% reduction in security breaches and a significant improvement in their compliance posture.
- Optimized Resource Utilization and Cost Savings: Remote monitoring software allows organizations to effectively manage resources, minimizing waste and optimizing utilization. A healthcare provider implemented remote monitoring software to track the performance of their medical equipment, leading to a 10% reduction in maintenance costs and a 5% increase in equipment uptime. This resulted in significant cost savings and improved patient care.
While the benefits are undeniable, organizations have also encountered challenges during implementation, including:
- Integration Complexity: Integrating remote monitoring software with existing systems can be complex, requiring careful planning and coordination to ensure seamless data flow and functionality.
- Data Overload and Alert Fatigue: Effective management of the large volume of data generated by remote monitoring software is crucial to avoid alert fatigue and ensure that critical alerts are not overlooked.
- Security Concerns: Ensuring the security of data transmitted and stored by remote monitoring software is paramount, requiring robust security measures and best practices to protect sensitive information.
Key Lessons Learned from Case Studies
Analyzing successful implementations of remote monitoring software reveals key lessons that organizations can leverage to maximize their adoption and benefits:
- Clear Objectives and Defined Scope: Establishing clear objectives and a well-defined scope for the implementation is essential to ensure that the software aligns with organizational goals and delivers tangible results.
- Comprehensive Planning and Stakeholder Engagement: Thorough planning, including stakeholder engagement and communication, is crucial for a successful implementation, minimizing disruptions and ensuring buy-in from all involved parties.
- Effective Training and Support: Providing comprehensive training and ongoing support to users is essential for maximizing the adoption and utilization of remote monitoring software, enabling them to effectively leverage its capabilities.
- Continuous Monitoring and Optimization: Regular monitoring and optimization of the software’s performance and configuration are critical for ensuring its effectiveness and maximizing its benefits over time.
Concluding Remarks
In conclusion, remote monitoring software is a powerful tool that empowers organizations to achieve unprecedented levels of operational excellence. By providing real-time visibility into their systems and applications, it enables proactive maintenance, reduces downtime, and enhances security. As technology continues to evolve, remote monitoring software will undoubtedly play an even more critical role in shaping the future of business operations.
Remote monitoring software allows you to keep tabs on your systems from anywhere, providing valuable insights into performance and security. If you need to remove any unwanted programs before installing remote monitoring software, consider using revo uninstaller free , a powerful tool for thorough uninstallation.
This ensures a clean slate for your remote monitoring software to operate efficiently.

