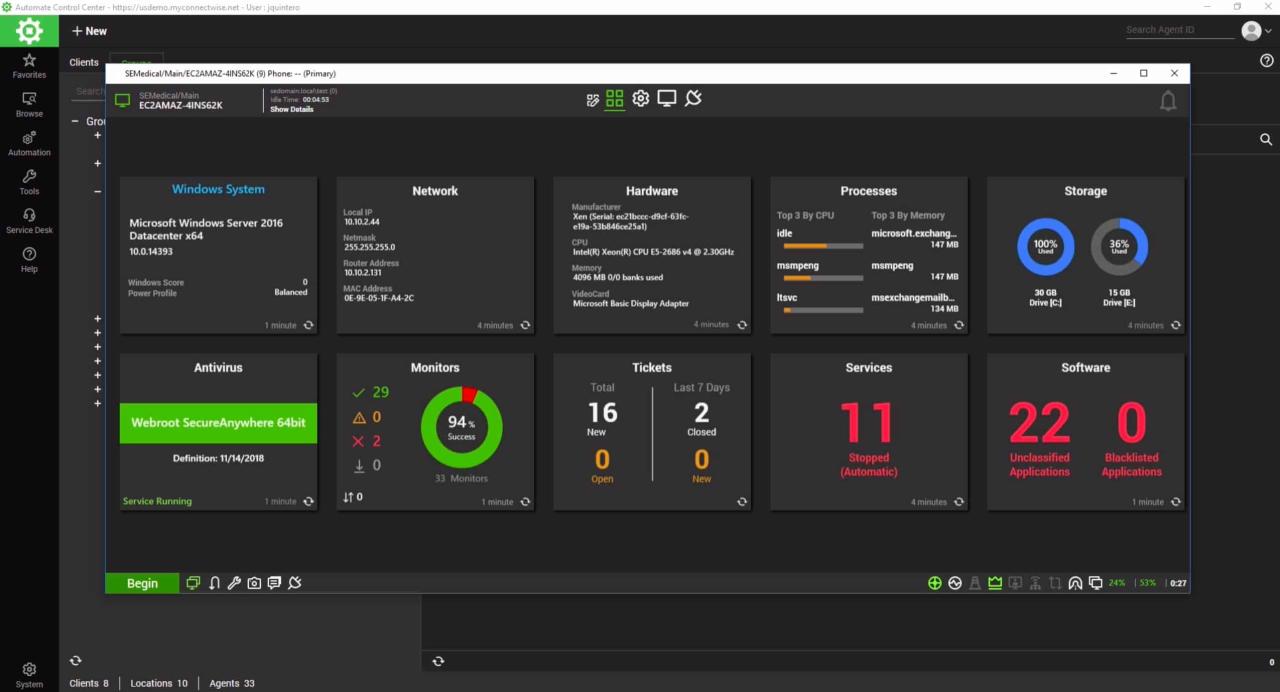
RMM software, or Remote Monitoring and Management software, has become a cornerstone for businesses seeking to optimize their IT infrastructure and ensure seamless operations. This sophisticated technology empowers organizations to remotely monitor and manage their computer systems, networks, and devices, providing a centralized platform for managing IT tasks and security.
Table of Contents
RMM software is a powerful tool that enables IT professionals to automate tasks, streamline processes, and proactively address potential issues. From monitoring system performance and security to deploying software updates and managing user accounts, RMM solutions offer a comprehensive suite of features designed to enhance IT efficiency and security.
What is RMM Software?
RMM software, short for Remote Monitoring and Management software, is a powerful tool designed to streamline and automate IT tasks for businesses of all sizes. It allows IT professionals to remotely monitor and manage computer systems, networks, and devices, ensuring smooth operations and minimizing downtime.
Core Functionalities
RMM software offers a comprehensive suite of functionalities to simplify IT management. These functionalities include:
- Remote Access and Control: RMM software provides secure access to remote computers, enabling IT teams to troubleshoot issues, install software, and perform other administrative tasks remotely. This eliminates the need for physical presence at each device, saving time and resources.
- Network Monitoring: RMM tools constantly monitor network performance, identifying potential bottlenecks and security threats. They can track bandwidth usage, detect network outages, and alert administrators to any anomalies.
- System Monitoring: RMM software continuously monitors the health of individual computers and servers. This includes monitoring CPU usage, memory utilization, disk space, and other critical system parameters. Alerts are triggered when thresholds are exceeded, allowing for proactive problem resolution.
- Patch Management: RMM tools automate the process of installing software updates and security patches. This ensures systems are protected from vulnerabilities and helps maintain compliance with industry standards.
- Security Management: RMM software plays a crucial role in safeguarding computer systems. They can enforce security policies, manage user accounts, and detect and respond to security threats in real-time.
- Reporting and Analytics: RMM software generates comprehensive reports on system performance, security events, and other relevant metrics. These reports provide valuable insights into IT operations, enabling better decision-making and resource allocation.
Common Tasks Automated by RMM Software
RMM software streamlines many common IT tasks, freeing up IT professionals to focus on strategic initiatives. Here are some examples:
- Software Deployment: RMM tools allow for automated software installation and updates across multiple devices, ensuring consistent application versions and minimizing user downtime.
- Backup and Disaster Recovery: RMM software automates data backups and disaster recovery procedures, ensuring data integrity and business continuity in case of system failures or security breaches.
- Endpoint Security: RMM software enforces security policies, such as password complexity requirements and antivirus updates, across all managed devices.
- User Account Management: RMM tools simplify user account creation, modification, and deletion, ensuring consistent access control and security.
- Asset Management: RMM software provides a centralized inventory of all managed devices, including hardware and software details, making it easier to track and manage assets.
Benefits of Using RMM Software
RMM software offers a wide range of benefits for businesses of all sizes. By streamlining IT operations, improving security, and reducing costs, RMM software can help businesses achieve their goals and stay ahead of the competition.
Improved IT Efficiency
RMM software helps businesses improve IT efficiency by automating tasks, providing real-time monitoring, and simplifying troubleshooting.
- Automated tasks: RMM software can automate repetitive tasks such as software updates, patch management, and system backups, freeing up IT staff to focus on more strategic initiatives. This automation reduces the risk of human error and ensures that critical tasks are completed on time.
- Real-time monitoring: RMM software provides real-time monitoring of devices and networks, allowing IT staff to identify and address issues before they impact users. This proactive approach helps prevent downtime and ensures that business operations remain uninterrupted.
- Simplified troubleshooting: RMM software provides detailed logs and reports that can help IT staff quickly identify the root cause of issues. This allows for faster resolution times and reduces the time spent on troubleshooting.
Reduced Costs
RMM software can help businesses reduce costs by streamlining IT operations, improving security, and minimizing downtime.
- Reduced IT staffing costs: By automating tasks and simplifying troubleshooting, RMM software can reduce the need for dedicated IT staff. This can lead to significant cost savings, especially for businesses with limited IT resources.
- Improved security: RMM software can help businesses improve security by providing real-time monitoring, automated patching, and endpoint security solutions. This reduces the risk of security breaches and the associated costs of data recovery and remediation.
- Minimized downtime: RMM software helps prevent downtime by proactively monitoring devices and networks, identifying issues before they impact users. This reduces the cost of lost productivity and business disruption.
Enhanced Security and Compliance
RMM software helps businesses enhance security and compliance by providing a centralized platform for managing security policies, monitoring devices, and responding to threats.
- Centralized security management: RMM software provides a single platform for managing security policies, configuring security settings, and monitoring device activity. This simplifies security management and reduces the risk of inconsistencies across the network.
- Automated patching: RMM software automates the process of applying security patches and updates, ensuring that devices are protected from the latest vulnerabilities. This reduces the risk of security breaches and helps businesses meet compliance requirements.
- Endpoint security solutions: RMM software often includes endpoint security solutions such as antivirus software, firewalls, and intrusion detection systems. These solutions help protect devices from malware and other threats, enhancing overall security posture.
Key Features of RMM Software
RMM software is designed to simplify and streamline IT management tasks, offering a wide range of features that can significantly improve efficiency and security. This software empowers IT professionals to effectively monitor, manage, and secure devices and networks remotely.
Remote Monitoring and Management
Remote monitoring and management (RMM) is a crucial aspect of IT operations, allowing IT professionals to proactively identify and address issues before they impact users.
- Real-time Monitoring: RMM software provides real-time insights into the health and performance of devices and networks, allowing IT teams to identify potential problems before they escalate.
- Remote Access and Control: IT professionals can remotely access and control devices, enabling them to troubleshoot issues, install software, and configure settings without physically being present.
- Automated Alerts and Notifications: RMM software can send automated alerts and notifications to IT teams when issues arise, ensuring prompt attention and resolution.
- Centralized Management: RMM solutions provide a centralized platform for managing multiple devices and networks, simplifying administration and reducing complexity.
Automated Patch Management and Software Updates
Patch management and software updates are critical for maintaining security and stability. RMM software automates these processes, ensuring that devices are protected from vulnerabilities and running the latest versions of software.
- Automated Patch Deployment: RMM software can automatically scan devices for missing patches and deploy updates, eliminating the need for manual intervention.
- Vulnerability Assessment: RMM solutions can assess devices for vulnerabilities and prioritize patches based on severity and risk, ensuring that critical issues are addressed first.
- Software Update Management: RMM software can manage software updates for various applications, ensuring that devices are running the latest versions of software and benefiting from new features and security enhancements.
- Compliance Reporting: RMM solutions can generate reports on patch compliance and software update status, demonstrating adherence to security and regulatory requirements.
Types of RMM Software
RMM software comes in various forms, each catering to specific needs and functionalities. Understanding these distinctions can help you choose the best solution for your business.
Cloud-Based RMM Solutions
Cloud-based RMM solutions are hosted on remote servers and accessed through the internet. This means you don’t need to install or manage any software on your own servers.
- Accessibility: One of the primary advantages of cloud-based RMM is its accessibility. You can manage your IT infrastructure from anywhere with an internet connection. This is particularly beneficial for businesses with remote teams or geographically dispersed offices.
- Scalability: Cloud-based RMM solutions are highly scalable. You can easily add or remove devices as your needs change, without worrying about server capacity or infrastructure limitations.
- Cost-Effectiveness: Cloud-based RMM solutions often have a lower upfront cost compared to on-premise options. You typically pay a monthly subscription fee based on the number of devices you manage.
- Automatic Updates: Cloud-based RMM providers handle updates and maintenance, ensuring you always have the latest features and security patches. This eliminates the need for manual updates and reduces the risk of vulnerabilities.
Example: Some popular cloud-based RMM solutions include Datto RMM, Kaseya, and ConnectWise Automate.
On-Premise RMM Solutions
On-premise RMM solutions are installed and managed on your own servers. This provides you with greater control over your data and infrastructure.
- Data Security: On-premise solutions offer greater control over data security, as your data is stored on your own servers. This can be crucial for businesses handling sensitive information.
- Customization: On-premise RMM solutions allow for greater customization. You can configure the software to meet your specific needs and integrate it with your existing systems.
- Offline Access: On-premise solutions provide offline access to your data, which can be essential for businesses operating in areas with limited internet connectivity.
Example: Some popular on-premise RMM solutions include SolarWinds N-central and NinjaOne.
Choosing the Right RMM Software
Selecting the right RMM software is crucial for businesses of all sizes, as it directly impacts the efficiency and effectiveness of IT management. The right solution can streamline operations, reduce costs, and improve overall IT security. However, with a plethora of RMM solutions available, making the right choice can be overwhelming. This section will provide a comprehensive checklist for selecting the ideal RMM solution, along with key factors to consider during evaluation and the importance of compatibility with existing systems.
Factors to Consider When Evaluating RMM Software
Evaluating RMM software options involves considering a variety of factors that align with your specific needs and goals. These factors include:
- Scalability: Choose software that can grow with your business. Consider the number of devices you need to manage and your future growth plans. A scalable solution can handle increasing demands without compromising performance.
- Pricing: RMM software pricing models vary, ranging from flat monthly fees to per-device charges. Evaluate different pricing structures to find one that fits your budget and aligns with your usage patterns.
- Features: The features offered by RMM software are crucial for managing IT infrastructure effectively. Consider features like remote access, patch management, vulnerability scanning, and endpoint security. Ensure the software includes the features you need to meet your specific requirements.
- Ease of Use: RMM software should be user-friendly and intuitive, even for non-technical users. Look for solutions with a clear interface, comprehensive documentation, and responsive customer support.
- Security: Security is paramount when managing IT systems. Choose software with robust security features, such as data encryption, two-factor authentication, and regular security updates.
- Reporting: Comprehensive reporting capabilities are essential for monitoring IT performance and identifying potential issues. Look for software that generates detailed reports on device status, security threats, and software updates.
- Customer Support: Reliable customer support is essential for addressing technical issues and getting the most out of your RMM software. Choose a provider with responsive support channels, such as email, phone, and live chat.
Compatibility and Integration with Existing Systems
Compatibility and seamless integration with your existing IT systems are crucial for a smooth transition and efficient management. Consider these factors:
- Operating Systems: Ensure the RMM software is compatible with the operating systems used in your IT environment. This includes desktop operating systems (Windows, macOS, Linux) and mobile operating systems (Android, iOS).
- Existing Tools: Consider how the RMM software integrates with your existing IT tools, such as ticketing systems, monitoring tools, and security solutions. Seamless integration minimizes conflicts and streamlines operations.
- API Integration: The ability to integrate with other tools via APIs (Application Programming Interfaces) allows for greater flexibility and automation. Look for software with a well-documented API and a range of integrations.
Checklist for Selecting the Right RMM Solution
Use this checklist to guide your evaluation process:
- Define your requirements: Clearly identify your specific needs, such as the number of devices to manage, the desired features, and your budget.
- Research RMM software options: Explore different RMM solutions, considering factors like features, pricing, and user reviews.
- Request demos and trials: Obtain demos or free trials of shortlisted RMM software to experience their functionality firsthand.
- Evaluate compatibility: Ensure the chosen software is compatible with your existing IT systems and operating systems.
- Consider integration: Assess how well the RMM software integrates with your existing IT tools and APIs.
- Review security features: Scrutinize the software’s security features, such as data encryption, two-factor authentication, and regular security updates.
- Check customer support: Investigate the provider’s customer support options, including response times, availability, and communication channels.
- Read user reviews: Gather insights from other users by reading reviews and testimonials about the RMM software you are considering.
- Compare pricing: Analyze the pricing models of different RMM solutions to find one that aligns with your budget and usage patterns.
- Make an informed decision: Based on your evaluation, choose the RMM software that best meets your requirements and provides the greatest value.
Implementing RMM Software
Implementing an RMM solution is a significant step in streamlining your IT management processes and improving overall security. This process involves careful planning, efficient execution, and continuous monitoring to ensure a smooth transition and maximize the benefits of your chosen RMM software.
Steps Involved in Implementing RMM Software
The implementation process typically involves several key steps.
- Define Your Requirements: Begin by clearly defining your IT management needs and goals. Identify the specific challenges you aim to address with RMM software, such as remote monitoring, patch management, software deployment, or endpoint security. This will help you select the right RMM solution that aligns with your organization’s specific requirements.
- Select and Purchase RMM Software: After identifying your needs, carefully evaluate different RMM solutions available in the market. Consider factors like features, pricing, scalability, integration capabilities, and customer support. Once you’ve chosen the best fit, purchase the software and obtain necessary licenses.
- Onboard Your Devices: The next step involves adding your managed devices to the RMM platform. This usually involves installing an agent on each device, which enables the RMM software to monitor and manage them remotely. Follow the vendor’s instructions for agent installation and configuration.
- Configure and Customize the RMM Software: After onboarding devices, customize the RMM software to match your organization’s specific requirements. This might involve setting up monitoring rules, creating automated tasks, defining access control policies, and configuring alerts for critical events.
- Train Your Team: Provide comprehensive training to your IT team on how to use the RMM software effectively. This training should cover key features, functionalities, troubleshooting techniques, and best practices. Ensure everyone is comfortable navigating the platform and performing essential tasks.
- Pilot Testing and Rollout: Before deploying the RMM software across your entire organization, conduct a pilot test on a small group of devices. This allows you to identify and resolve any potential issues before going live. Once the pilot test is successful, gradually roll out the RMM software to the rest of your devices.
- Continuous Monitoring and Optimization: After implementation, continuously monitor the RMM software’s performance and make necessary adjustments. Analyze data, identify areas for improvement, and refine your configuration based on feedback and ongoing needs. Regularly update the software to benefit from new features and security patches.
Best Practices for Onboarding and Training Users
Effective onboarding and training are crucial for maximizing the benefits of your RMM software.
- Provide Clear and Concise Documentation: Create comprehensive user manuals, quick start guides, and online tutorials that cover all aspects of the RMM software. Use plain language, clear visuals, and step-by-step instructions to ensure easy understanding.
- Offer Hands-on Training: Organize interactive training sessions that allow users to practice using the RMM software in a controlled environment. This could involve live demonstrations, guided exercises, and Q&A sessions to address specific user queries.
- Create a Knowledge Base: Establish a central repository for user guides, FAQs, troubleshooting tips, and other relevant information. This knowledge base should be easily accessible and searchable, allowing users to find answers to their questions quickly and efficiently.
- Provide Ongoing Support: Offer ongoing support to users through email, phone, or chat. This could involve technical assistance, troubleshooting guidance, and answering questions related to the RMM software. Encourage users to report any issues or suggestions for improvement.
Configuring and Customizing the RMM Software
Configuration and customization are essential for tailoring the RMM software to your specific needs.
- Define Monitoring Rules: Set up monitoring rules to track key performance indicators (KPIs) and identify potential issues proactively. This might involve monitoring system resources, software updates, security events, or network activity.
- Create Automated Tasks: Automate repetitive tasks like software deployment, patch management, or script execution. This saves time, reduces errors, and improves efficiency.
- Configure Alerts and Notifications: Set up alerts and notifications to inform your IT team about critical events, such as system failures, security breaches, or software updates. This ensures timely intervention and minimizes downtime.
- Establish Access Control Policies: Define access control policies to restrict user access to specific features or devices based on their roles and responsibilities. This ensures data security and prevents unauthorized modifications.
- Integrate with Other Tools: Leverage the RMM software’s integration capabilities to connect with other tools in your IT infrastructure, such as ticketing systems, monitoring dashboards, or security platforms. This allows for seamless data sharing and improved workflow efficiency.
Future Trends in RMM Software
RMM software is constantly evolving to meet the changing needs of IT professionals. The future of RMM software is bright, with several exciting trends on the horizon. These trends are driven by advancements in technology, particularly in the areas of artificial intelligence (AI) and machine learning (ML). These advancements are enabling RMM software to become more intelligent, automated, and proactive in managing IT infrastructure.
Impact of AI and ML on RMM Software
AI and ML are transforming RMM software by enabling it to analyze vast amounts of data, identify patterns, and make predictions. These capabilities allow RMM software to automate tasks, proactively identify and resolve issues, and improve security posture.
- Predictive Maintenance: AI and ML algorithms can analyze historical data to predict when devices are likely to fail. This allows IT professionals to proactively schedule maintenance and prevent downtime. For example, an RMM tool can analyze the performance metrics of a server over time and predict when its hard drive is likely to fail. Based on this prediction, the IT team can proactively replace the hard drive before it fails, preventing potential data loss and downtime.
- Automated Threat Detection and Response: AI and ML can help RMM software detect and respond to security threats in real-time. By analyzing network traffic and user behavior, RMM software can identify suspicious activity and automatically take action to mitigate the threat. For example, an RMM tool can detect a malware attack on a user’s computer and automatically quarantine the infected device to prevent the spread of malware. This can significantly reduce the risk of data breaches and other security incidents.
- Personalized IT Support: AI and ML can be used to personalize IT support experiences. By analyzing user data, RMM software can provide tailored recommendations and support based on individual needs. For example, an RMM tool can analyze a user’s past support requests and provide them with relevant articles and FAQs. This can help users resolve issues more quickly and efficiently.
Addressing Future IT Challenges
RMM software is playing a crucial role in helping IT professionals address the challenges of managing increasingly complex IT environments. As technology continues to evolve, RMM software will need to adapt to meet new challenges.
- The Rise of Cloud Computing: The increasing adoption of cloud computing is creating new challenges for IT professionals. RMM software needs to be able to manage and monitor cloud-based resources effectively. This includes managing cloud security, ensuring compliance with regulations, and optimizing cloud performance.
- The Internet of Things (IoT): The growing number of connected devices is creating a new wave of security and management challenges. RMM software needs to be able to manage and secure IoT devices effectively. This includes managing device updates, ensuring data security, and preventing unauthorized access.
- The Growing Importance of Cybersecurity: Cyberattacks are becoming increasingly sophisticated and frequent. RMM software needs to be able to protect against these attacks effectively. This includes implementing robust security measures, monitoring for suspicious activity, and responding quickly to security incidents.
RMM Software and Cybersecurity
RMM software plays a crucial role in enhancing the cybersecurity posture of organizations by automating security tasks, providing centralized visibility into security events, and offering proactive security measures. This integration strengthens an organization’s overall security strategy, making it more resilient against evolving cyber threats.
Detection and Response to Security Threats
RMM software empowers organizations to proactively detect and respond to security threats through various mechanisms. By leveraging real-time monitoring, vulnerability assessments, and automated patching, RMM software can identify potential security risks before they escalate into major incidents.
- Real-time Monitoring: RMM software continuously monitors endpoints for suspicious activity, such as unauthorized access attempts, malware infections, or unusual network traffic. This continuous surveillance allows for early detection and timely response to security threats.
- Vulnerability Assessments: RMM software can scan endpoints for known vulnerabilities and provide detailed reports outlining the severity and potential impact of each vulnerability. This information enables organizations to prioritize patching efforts and address critical vulnerabilities promptly.
- Automated Patching: RMM software can automate the patching process, ensuring that endpoints are updated with the latest security patches and updates. This reduces the risk of exploiting known vulnerabilities, making the organization less susceptible to attacks.
RMM Features for Enhanced Security and Compliance
RMM software incorporates various features that strengthen security and compliance, contributing to a more robust and secure IT environment.
- Endpoint Security Policies: RMM software allows organizations to define and enforce comprehensive endpoint security policies, including password complexity requirements, firewall settings, and access control restrictions. These policies help to prevent unauthorized access and mitigate security risks.
- Antivirus and Anti-malware Protection: RMM software can integrate with antivirus and anti-malware solutions, providing centralized management and monitoring of endpoint protection. This ensures that endpoints are protected from known and emerging threats.
- Data Encryption and Backup: RMM software can encrypt sensitive data stored on endpoints, safeguarding it from unauthorized access. Additionally, it can automate data backups, ensuring that critical data is protected against accidental loss or malicious attacks.
- Security Auditing and Reporting: RMM software provides comprehensive security auditing and reporting capabilities, allowing organizations to track security events, identify security trends, and assess the effectiveness of their security measures. This information helps organizations to improve their security posture and comply with relevant regulations.
RMM Software and Remote Work
The rise of remote work has transformed the modern workplace, and with it comes a new set of challenges for IT teams. Managing and securing devices spread across various locations requires a robust solution, and RMM software has emerged as a critical tool in this landscape.
Impact of RMM Software on Remote Work Environments
RMM software has a profound impact on remote work environments, enabling IT teams to effectively manage and support remote employees. By centralizing device management, security, and support, RMM software streamlines operations and enhances productivity for both employees and IT staff.
Facilitating Secure and Efficient Remote Access
RMM software plays a vital role in ensuring secure and efficient remote access for employees. Its key features include:
- Remote Desktop Access: RMM software enables IT staff to remotely access and control employee devices, providing real-time support and troubleshooting.
- Secure Data Transfer: RMM software employs encryption and secure protocols to protect sensitive data during remote access and data transfer.
- Multi-factor Authentication: RMM platforms often integrate multi-factor authentication, adding an extra layer of security to remote access.
- Remote Software Deployment and Updates: RMM software allows for seamless deployment and updates of software on remote devices, ensuring consistency and security across the network.
Managing Remote Devices with RMM Software
Managing remote devices effectively presents both challenges and opportunities. RMM software addresses these challenges by:
- Centralized Management: RMM platforms provide a single dashboard for managing all remote devices, simplifying administration and reducing complexity.
- Automated Patch Management: RMM software automates patch management for operating systems and applications, ensuring that devices are protected against vulnerabilities.
- Real-time Monitoring and Alerts: RMM platforms monitor device health, performance, and security, providing real-time alerts to IT staff for prompt intervention.
- Remote Device Control: RMM software enables IT teams to remotely lock, wipe, or disable devices in case of loss or theft, protecting sensitive data.
RMM Software for Different Industries
RMM software offers valuable solutions for various industries, catering to their unique needs and challenges. The adaptability of RMM software allows businesses to streamline operations, improve efficiency, and enhance security across diverse sectors.
Healthcare
RMM software plays a crucial role in healthcare, ensuring the secure and reliable operation of medical devices, electronic health records (EHRs), and patient data.
- Patient Data Security: RMM software enforces strong security measures to protect sensitive patient information from unauthorized access and cyberattacks. This is critical in meeting HIPAA compliance requirements.
- Remote Monitoring of Medical Devices: RMM tools enable remote monitoring of medical devices, allowing healthcare providers to proactively identify and address potential issues, ensuring uninterrupted patient care.
- Automated Patch Management: RMM software automates patch management for medical devices and software, reducing vulnerabilities and ensuring compliance with industry regulations.
Financial Services
RMM software is essential for financial institutions, where security and compliance are paramount.
- Compliance with Regulatory Standards: RMM software helps financial institutions meet stringent compliance requirements, such as PCI DSS and SOX, by providing automated security controls and audit trails.
- Secure Remote Access: RMM tools enable secure remote access for employees, ensuring that sensitive financial data is protected during remote work.
- Disaster Recovery and Business Continuity: RMM software facilitates quick and efficient disaster recovery, ensuring business continuity in the event of a system outage or cyberattack.
Education
RMM software helps educational institutions manage their IT infrastructure efficiently and securely, ensuring smooth learning environments for students.
- Remote Learning Support: RMM tools facilitate remote learning by providing secure access to educational resources and applications for students and teachers.
- Device Management: RMM software simplifies device management for schools and universities, ensuring that devices are up-to-date and secure.
- Network Monitoring: RMM tools provide real-time network monitoring, allowing educational institutions to identify and resolve connectivity issues promptly.
Manufacturing
RMM software is crucial for manufacturers, enabling them to optimize their production processes and maintain operational efficiency.
- Industrial Control System (ICS) Security: RMM software protects industrial control systems from cyberattacks, ensuring the safety and reliability of manufacturing operations.
- Remote Monitoring and Management of Manufacturing Equipment: RMM tools enable remote monitoring and management of manufacturing equipment, allowing for proactive maintenance and troubleshooting.
- Data Backup and Disaster Recovery: RMM software ensures the security and availability of critical manufacturing data through automated backups and disaster recovery plans.
Retail
RMM software helps retailers enhance their customer experience and optimize their operations by ensuring secure and reliable IT infrastructure.
- Point-of-Sale (POS) System Security: RMM software secures POS systems, protecting customer payment information and preventing fraudulent transactions.
- Inventory Management: RMM tools enable remote monitoring of inventory levels and automate inventory management processes, improving efficiency and reducing costs.
- Customer Support: RMM software facilitates remote customer support, allowing retailers to resolve technical issues quickly and efficiently.
Last Recap
The adoption of RMM software signifies a shift towards proactive and intelligent IT management. By leveraging the power of automation, remote access, and comprehensive monitoring, businesses can gain valuable insights into their IT environment, optimize performance, and mitigate potential risks. RMM solutions are not merely tools for managing devices; they are strategic assets that empower businesses to achieve their IT goals and drive success.
RMM software helps manage IT systems remotely, offering features like patch management, endpoint security, and remote control. While many RMM solutions offer remote control capabilities, some prefer to use dedicated tools like teamviewer 15 for its user-friendly interface and robust features.
Integrating TeamViewer into an RMM workflow can streamline remote support and enhance overall IT management efficiency.