RMM software solutions have revolutionized the way businesses manage their IT infrastructure, offering a comprehensive suite of tools to monitor, manage, and secure endpoints remotely. From proactive maintenance to robust security measures, RMM solutions empower IT teams to optimize performance, minimize downtime, and safeguard against evolving cyber threats.
Table of Contents
This comprehensive guide delves into the world of RMM software, exploring its key features, benefits, and implementation considerations. We’ll discuss how RMM solutions can transform IT operations, enhance efficiency, and contribute to a more secure and resilient business environment.
Introduction to RMM Software Solutions
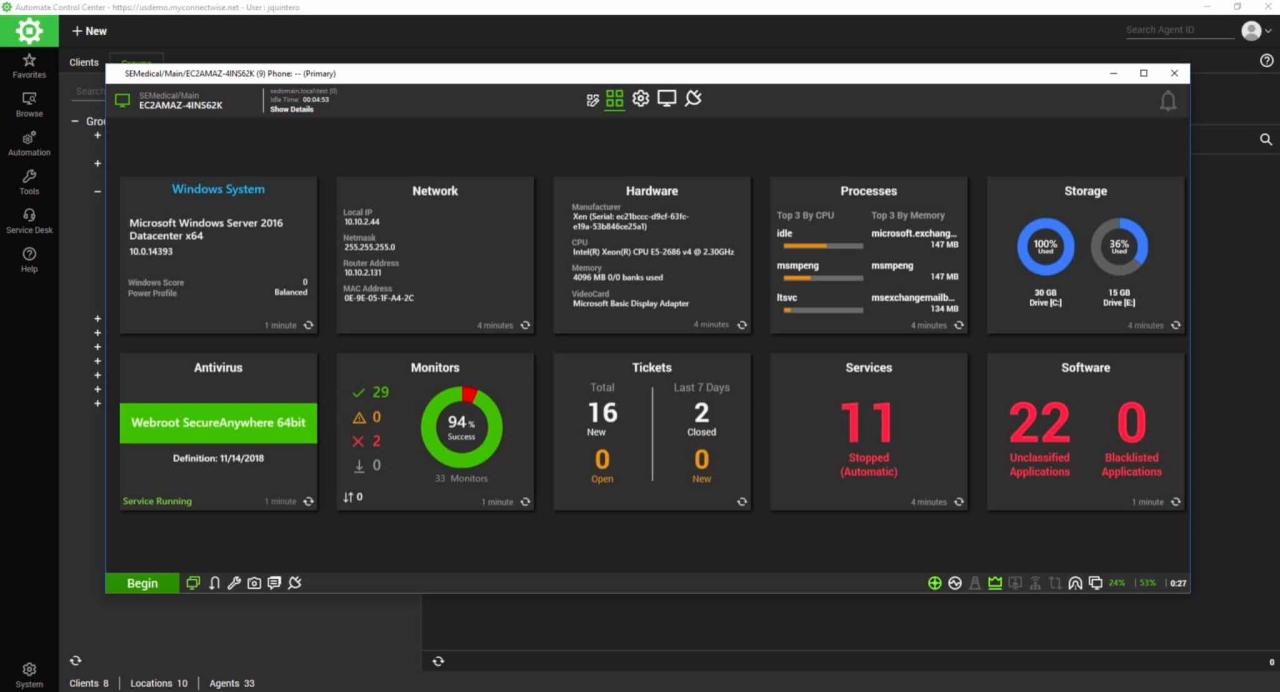
RMM, or Remote Monitoring and Management software, is a category of IT tools that allows businesses to manage and monitor their computer systems remotely. RMM solutions offer a wide range of functionalities that can streamline IT operations, enhance security, and improve overall system performance.
RMM solutions provide businesses with a centralized platform to manage their IT infrastructure, regardless of location. This remote access and control capability empowers IT professionals to proactively address issues, optimize performance, and ensure business continuity.
Benefits of RMM Software Solutions
The adoption of RMM solutions offers businesses numerous advantages, contributing to increased efficiency, improved security, and reduced operational costs.
- Improved IT Efficiency: RMM software automates routine tasks such as software updates, patch management, and system backups, freeing up IT staff to focus on more strategic initiatives.
- Enhanced Security Posture: RMM solutions help businesses strengthen their security posture by detecting and mitigating potential threats, implementing security policies, and monitoring for vulnerabilities.
- Reduced IT Costs: By automating tasks and streamlining processes, RMM software can significantly reduce IT operational costs. This includes minimizing downtime, reducing the need for on-site visits, and optimizing resource allocation.
- Improved System Performance: RMM solutions monitor system performance metrics, identify bottlenecks, and optimize resource allocation to ensure smooth and efficient operation.
- Enhanced Compliance: RMM software helps businesses comply with industry regulations and data privacy standards by providing tools for data encryption, access control, and audit logging.
Types of RMM Software
RMM solutions are available in various forms, catering to different business needs and IT infrastructure configurations.
- Cloud-Based RMM: Cloud-based RMM solutions are hosted on a third-party server, accessible through a web browser or mobile app. This model offers scalability, accessibility, and ease of deployment, making it suitable for businesses of all sizes.
- On-Premise RMM: On-premise RMM solutions are installed and managed on the company’s own servers. This model provides greater control over data security and privacy, but requires more technical expertise for setup and maintenance.
- Hybrid RMM: Hybrid RMM solutions combine the benefits of both cloud-based and on-premise models, offering flexibility and scalability while maintaining a degree of control over data.
Key Features of RMM Software
RMM software is designed to streamline IT management and improve operational efficiency. It provides a comprehensive suite of tools that enable IT professionals to monitor, manage, and secure endpoints remotely. These features are crucial for organizations of all sizes, as they help ensure smooth operations, minimize downtime, and enhance security posture.
Remote Monitoring and Management, Rmm software solutions
Remote monitoring and management (RMM) is the core functionality of RMM software. This feature allows IT professionals to monitor and manage endpoints remotely, regardless of their physical location. RMM tools can collect real-time data on system performance, hardware health, and software updates. This information helps IT teams identify potential issues before they escalate into major problems, reducing downtime and improving overall system stability.
- Real-time System Monitoring: RMM software provides real-time insights into system performance metrics, such as CPU usage, memory utilization, disk space, and network activity. This allows IT professionals to identify potential bottlenecks and resource constraints proactively.
- Hardware Health Monitoring: RMM tools can monitor hardware components, including hard drives, RAM, and network adapters, for signs of failure. This enables early detection of hardware issues and allows for timely replacement, minimizing downtime and data loss.
- Software Update Management: RMM software facilitates software update management, ensuring that all endpoints are running the latest versions of operating systems and applications. This helps mitigate security vulnerabilities and improve system performance.
Patch Management
Patch management is a critical aspect of cybersecurity. RMM software automates the process of identifying, downloading, and applying software patches to all endpoints. This ensures that systems are protected against known vulnerabilities and reduces the risk of security breaches.
- Automated Patch Scanning: RMM software regularly scans endpoints for missing or outdated patches. It identifies vulnerabilities and prioritizes patching based on severity and risk.
- Patch Deployment: RMM tools automate patch deployment, ensuring that all endpoints receive the necessary updates in a timely manner. This eliminates manual intervention and reduces the risk of human error.
- Patch Compliance Reporting: RMM software provides comprehensive reports on patch compliance, allowing IT teams to track the status of patch deployments and identify any gaps in security.
Endpoint Security
Endpoint security is essential for protecting sensitive data and preventing malware infections. RMM software offers various endpoint security features, including antivirus protection, firewall management, and intrusion detection.
- Antivirus Protection: RMM tools integrate with antivirus software to provide real-time protection against malware threats. They can scan endpoints for malicious software, quarantine infected files, and prevent future infections.
- Firewall Management: RMM software allows IT teams to configure and manage firewalls on endpoints, controlling network access and preventing unauthorized connections.
- Intrusion Detection: RMM tools monitor network traffic for suspicious activity and detect potential intrusions. They can alert IT teams to security threats and provide insights into attack methods.
Vulnerability Scanning
Vulnerability scanning is a proactive approach to identify security weaknesses in endpoints and networks. RMM software includes vulnerability scanning tools that can detect and prioritize vulnerabilities, enabling IT teams to address them before they are exploited by attackers.
- Automated Vulnerability Scanning: RMM software automatically scans endpoints and networks for known vulnerabilities. It identifies security gaps and provides detailed information about the risks associated with each vulnerability.
- Vulnerability Prioritization: RMM tools prioritize vulnerabilities based on severity and exploitability, allowing IT teams to focus on the most critical issues first.
- Vulnerability Remediation: RMM software provides guidance and resources for remediating vulnerabilities, including patch updates, configuration changes, and security hardening techniques.
Asset Management
Asset management is a crucial part of IT operations, enabling organizations to track and manage their IT assets, including hardware, software, and licenses. RMM software provides asset management capabilities that streamline this process and improve IT efficiency.
- Asset Inventory: RMM tools automatically discover and inventory IT assets, providing a comprehensive list of all hardware and software components in the organization’s network.
- Asset Tracking: RMM software tracks the location, status, and usage of IT assets, enabling IT teams to manage their inventory effectively.
- Asset Lifecycle Management: RMM tools help IT teams manage the lifecycle of IT assets, from procurement to disposal, ensuring compliance with regulatory requirements and maximizing asset utilization.
Reporting
RMM software provides comprehensive reporting capabilities that enable IT teams to track key performance indicators (KPIs), identify trends, and make informed decisions.
- Performance Reports: RMM tools generate reports on system performance, hardware health, and software usage, providing insights into the overall health and efficiency of IT infrastructure.
- Security Reports: RMM software generates reports on security vulnerabilities, patch compliance, and intrusion attempts, providing a comprehensive overview of the organization’s security posture.
- Asset Management Reports: RMM tools provide reports on asset inventory, usage, and lifecycle, helping IT teams optimize asset utilization and ensure compliance with regulations.
Ticketing Systems
RMM software often includes integrated ticketing systems that facilitate communication and collaboration between IT teams and end-users.
- Issue Tracking: RMM tools enable IT teams to track and manage IT issues reported by end-users, ensuring that all problems are addressed promptly and efficiently.
- Communication and Collaboration: RMM software facilitates communication between IT teams and end-users, providing a centralized platform for resolving IT issues and sharing updates.
- Service Level Agreements (SLAs): RMM tools can be used to track and enforce SLAs, ensuring that IT services meet agreed-upon performance standards.
Concluding Remarks: Rmm Software Solutions

In conclusion, RMM software solutions have emerged as a vital asset for modern businesses seeking to optimize their IT infrastructure and achieve greater efficiency, security, and cost-effectiveness. By leveraging the power of remote monitoring, automated management, and proactive security measures, RMM solutions empower IT teams to proactively address challenges, minimize downtime, and protect against emerging threats. As the technology landscape continues to evolve, RMM software will play an increasingly important role in shaping the future of IT management.
RMM software solutions can help businesses streamline their IT operations and manage their devices effectively. If you’re looking for a way to easily input Bangla text on your computer, you can download the popular Bijoy Bayanno software from this website.
Once you’ve got that sorted, you can focus on choosing the right RMM solution for your specific needs and budget.
