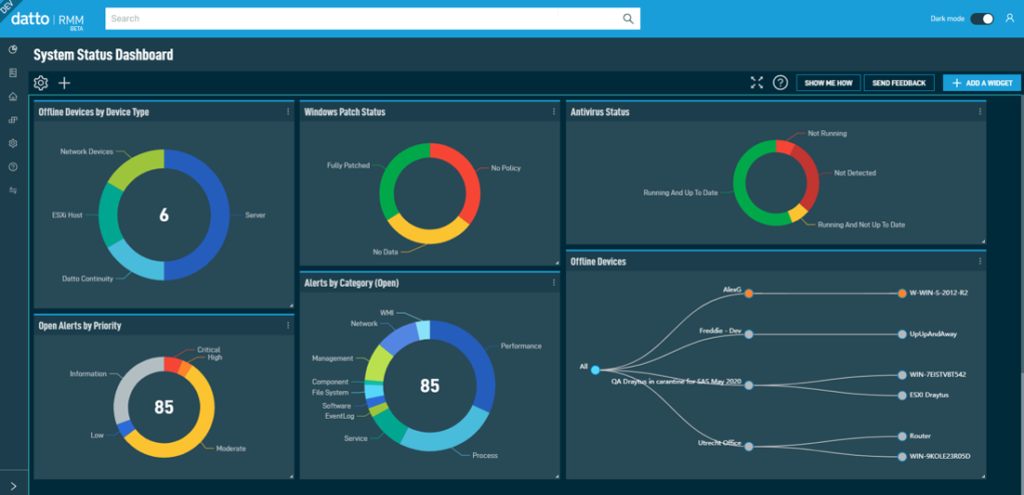
Software RMM, or Remote Monitoring and Management, is a game-changer for businesses seeking to optimize their IT infrastructure. This powerful suite of tools empowers organizations to remotely monitor, manage, and secure their systems, all from a centralized dashboard. Imagine having real-time insights into your network, proactively identifying potential issues before they impact operations, and effortlessly patching vulnerabilities before attackers can exploit them. RMM software goes beyond basic monitoring, offering a comprehensive solution that encompasses everything from endpoint security and patch management to asset tracking and automated tasks.
Table of Contents
The beauty of RMM lies in its ability to streamline IT operations, reducing manual efforts and freeing up valuable time for more strategic initiatives. With automated tasks and proactive alerts, IT teams can focus on what matters most: driving business growth and innovation. Whether you’re a small business with limited IT resources or a large enterprise with a complex IT environment, RMM software can significantly enhance your IT efficiency and security posture.
Types of RMM Software
RMM software, or Remote Monitoring and Management software, is a powerful tool for IT professionals to manage and monitor their clients’ computer systems remotely. These solutions encompass a wide range of features and functionalities, which can be categorized based on their deployment models and the specific types of services they offer.
Deployment Models
Different RMM software solutions are deployed using various models, each with its own advantages and disadvantages. The two main deployment models are cloud-based and on-premises.
- Cloud-based RMM: This model involves hosting the RMM software on a cloud server, accessible via a web browser or dedicated client application. This approach eliminates the need for on-site infrastructure and offers scalability, flexibility, and accessibility from anywhere with an internet connection. Popular cloud-based RMM solutions include ConnectWise Manage, Datto RMM, and Kaseya VSA.
- On-premises RMM: In this model, the RMM software is installed and managed directly on the IT provider’s servers. This approach provides greater control over the software and data, but it requires more technical expertise and ongoing maintenance. Some popular on-premises RMM solutions include SolarWinds N-central, Atera, and NinjaOne.
Types of RMM Solutions
RMM software can be further categorized based on the specific services they offer. Common types of RMM solutions include:
- Endpoint Management: This type of RMM solution provides tools for managing and monitoring endpoints, including computers, laptops, servers, and mobile devices. These solutions offer features like software deployment, inventory management, remote control, and security policy enforcement.
- Patch Management: Patch management RMM solutions automate the process of identifying, downloading, and applying software updates and security patches to endpoints. This helps ensure systems are protected against vulnerabilities and malware.
- Remote Access: This type of RMM solution enables IT professionals to access and control endpoints remotely. This allows them to troubleshoot issues, provide technical support, and perform other tasks without physically being on-site.
- Security Monitoring: Security monitoring RMM solutions provide real-time insights into the security posture of endpoints. These solutions monitor for suspicious activity, malware infections, and other security threats, enabling proactive threat detection and response.
- Reporting and Analytics: Many RMM solutions offer robust reporting and analytics capabilities. This allows IT professionals to track key metrics, identify trends, and make data-driven decisions about their IT infrastructure.
Popular RMM Software Vendors
Numerous vendors offer RMM software solutions, each with its own unique features and capabilities. Some popular RMM software vendors include:
- ConnectWise Manage: A comprehensive RMM solution that offers a wide range of features, including endpoint management, patch management, remote access, and security monitoring. ConnectWise Manage is a cloud-based solution designed for managed service providers (MSPs).
- Datto RMM: Another cloud-based RMM solution known for its user-friendly interface and robust features. Datto RMM is designed for MSPs and focuses on automation, efficiency, and security.
- Kaseya VSA: A powerful on-premises RMM solution that offers a wide range of features, including endpoint management, patch management, remote access, and security monitoring. Kaseya VSA is a popular choice for larger IT organizations.
- SolarWinds N-central: An on-premises RMM solution known for its comprehensive features and strong reporting capabilities. SolarWinds N-central is a good choice for organizations that need a robust RMM solution with advanced monitoring and analytics features.
- Atera: A cloud-based RMM solution that is known for its affordability and ease of use. Atera is a good option for smaller businesses and MSPs that are looking for a simple and affordable RMM solution.
- NinjaOne: A cloud-based RMM solution that offers a wide range of features, including endpoint management, patch management, remote access, and security monitoring. NinjaOne is known for its strong focus on automation and its user-friendly interface.
Choosing the Right RMM Software
Selecting the right RMM software is crucial for optimizing IT operations and ensuring the security of your organization’s devices and data. This decision requires a comprehensive evaluation process that considers your specific needs, budget, and long-term goals.
Factors to Consider
Before diving into the details of specific features and pricing, it’s essential to define your core requirements. These factors will guide your evaluation and help you narrow down the options.
- Scalability: Consider your current and future needs. Choose software that can accommodate your growth and expansion plans.
- Security: RMM software should offer robust security features to protect your devices and data from cyber threats.
- Compliance: If your industry has specific compliance regulations, ensure the RMM solution meets those requirements.
- Integration: Consider how well the RMM software integrates with your existing IT infrastructure and tools.
- Support: Look for a vendor that offers reliable and responsive support services.
Evaluating Software Features
Once you have a clear understanding of your needs, it’s time to evaluate the features offered by different RMM solutions.
- Remote Access and Control: This feature allows you to remotely access and control devices, troubleshoot issues, and install software updates.
- Patch Management: Automatic patch management ensures that your devices are always up-to-date with the latest security updates.
- Endpoint Security: Look for features that protect your devices from malware, viruses, and other threats.
- Asset Management: This feature helps you track and manage your IT assets, including hardware, software, and licenses.
- Reporting and Analytics: Robust reporting capabilities allow you to monitor system performance, identify potential issues, and make informed decisions.
Pricing and Support Services
Pricing is a significant factor to consider, but it’s crucial to look beyond the initial cost.
- Pricing Models: Different vendors offer various pricing models, including per-device, per-technician, or flat-rate subscriptions.
- Support Levels: Evaluate the level of support offered, including response times, availability of technical experts, and knowledge base resources.
- Hidden Costs: Be aware of any hidden costs, such as additional fees for features, integrations, or training.
Vendor Evaluation and Comparison
To make an informed decision, conduct a thorough vendor evaluation and comparison.
- Request Demos: Request demos from shortlisted vendors to see the software in action and ask specific questions.
- Read Reviews: Consult online reviews and industry reports to get insights from other users.
- Trial Periods: Take advantage of free trial periods to test the software in your own environment.
- Compare Features: Create a spreadsheet or chart to compare the features, pricing, and support services offered by different vendors.
Implementing RMM Software
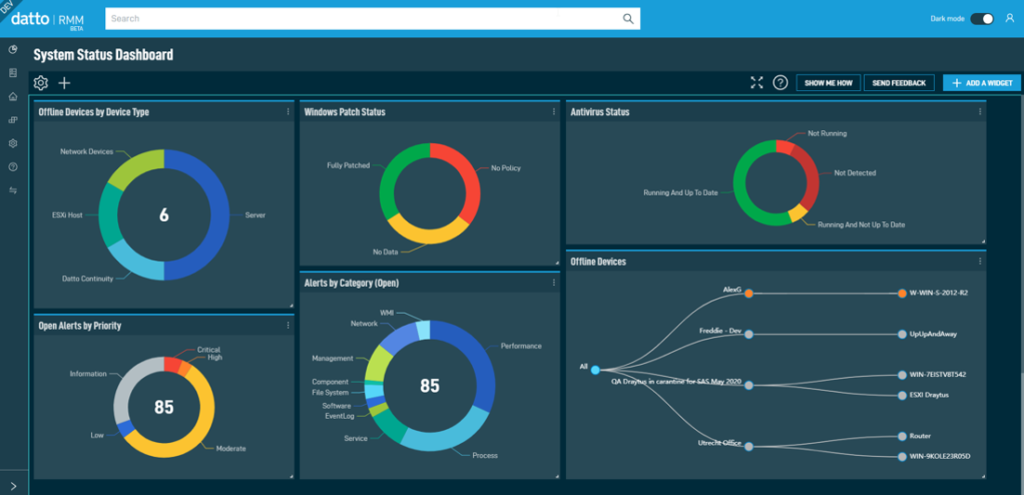
Implementing RMM software is the next crucial step after choosing the right solution. This involves a systematic process of deploying and configuring the software, integrating it with your existing IT infrastructure, and training your IT staff to use it effectively.
Deployment and Configuration
Deployment and configuration of RMM software are crucial for its successful implementation. This process involves several steps, starting with the initial setup and installation, followed by agent deployment on managed devices and customizing the software to meet your specific requirements.
- Initial Setup and Installation: The first step is to install the RMM software on a server or cloud platform. This usually involves downloading the software, configuring it with your organization’s details, and setting up a database to store data.
- Agent Deployment: After installing the RMM software, you need to deploy agents on all devices you want to manage. These agents collect data and execute commands from the central server, allowing the RMM software to monitor and control the devices. The deployment process can vary depending on the RMM software, but it often involves downloading the agent installer, running it on the target device, and configuring the agent to connect to the central server.
- Configuration and Customization: Once the agents are deployed, you can configure and customize the RMM software to meet your specific needs. This may include defining monitoring policies, setting up alerts and notifications, configuring remote access, and automating tasks. You can also customize the software’s interface and reporting features to make it more user-friendly for your IT staff.
Integration with Existing IT Infrastructure
Integrating RMM software with your existing IT infrastructure is essential for ensuring seamless operation and avoiding conflicts. This involves connecting the RMM software to your existing systems, such as your active directory, ticketing system, and monitoring tools.
- Active Directory Integration: Integrating the RMM software with your Active Directory can automate user account management and simplify device deployment. This allows the RMM software to automatically discover and manage devices connected to your network and assign users access based on their Active Directory permissions.
- Ticketing System Integration: Integrating the RMM software with your ticketing system can help streamline your IT support process. This allows you to automatically create tickets in your ticketing system when an alert is triggered in the RMM software, and it also enables you to manage and resolve issues directly within the RMM software.
- Monitoring Tool Integration: Integrating the RMM software with your existing monitoring tools can provide a comprehensive view of your IT infrastructure. This allows you to correlate data from the RMM software with other monitoring tools, providing a more complete understanding of your system’s health and performance.
Training IT Staff
Training your IT staff is essential for them to effectively use and manage the RMM software. This involves providing them with the necessary knowledge and skills to understand the software’s features, configure it, and troubleshoot issues.
- Software Training: Training should include an overview of the RMM software’s features and functionalities, including how to monitor devices, manage patches, automate tasks, and generate reports.
- Hands-on Practice: Provide hands-on practice sessions where IT staff can work with the RMM software in a simulated environment. This allows them to learn how to use the software’s features and apply their knowledge to real-world scenarios.
- Ongoing Support: Provide ongoing support to IT staff after the initial training. This can include access to documentation, online resources, and dedicated support channels.
Case Studies and Success Stories
RMM software has revolutionized the way businesses manage their IT infrastructure, leading to significant improvements in efficiency, security, and cost savings. Let’s explore real-world examples of how businesses have successfully implemented RMM solutions and the positive outcomes they have achieved.
Benefits of RMM Software for Different Business Types
The benefits of RMM software are not limited to a specific industry or business size. Here are some examples of how RMM has helped businesses across various sectors:
- Healthcare: A small healthcare clinic implemented RMM to automate routine tasks like software updates and patch management. This freed up their IT staff to focus on more critical tasks, improving patient care and reducing downtime.
- Education: A large school district deployed RMM to manage a vast network of computers and devices. This centralized management system allowed them to quickly resolve issues, improve security, and ensure compliance with industry regulations.
- Manufacturing: A manufacturing company used RMM to monitor and optimize their production line equipment. By remotely monitoring the health of their machines, they were able to prevent costly downtime and improve overall efficiency.
Successful RMM Implementations and Positive Outcomes
Several businesses have successfully implemented RMM software, leading to remarkable improvements in their IT operations:
- Improved IT Efficiency: A retail chain implemented RMM to automate routine tasks, freeing up their IT staff to focus on strategic initiatives. This resulted in a 20% reduction in IT support costs and a 15% increase in employee productivity.
- Enhanced Security Posture: A financial services company deployed RMM to strengthen their security posture. The automated vulnerability scanning and patching capabilities helped them identify and mitigate security risks, reducing their exposure to cyberattacks.
- Reduced Downtime: A technology consulting firm implemented RMM to proactively monitor their client’s IT infrastructure. This enabled them to identify and resolve issues before they impacted their clients’ operations, significantly reducing downtime and improving customer satisfaction.
Challenges and Solutions Encountered During RMM Deployment, Software rmm
While RMM software offers numerous benefits, businesses may encounter challenges during its implementation:
- Integration with Existing Systems: Integrating RMM software with existing systems can be complex, requiring careful planning and execution. Solutions: Choose an RMM solution with robust integration capabilities and engage with experienced IT professionals for seamless integration.
- User Adoption: Ensuring user adoption can be challenging, especially if the RMM solution involves changes in workflows or procedures. Solutions: Provide comprehensive training and support to users, and involve them in the implementation process to foster buy-in and ownership.
- Data Security and Compliance: Businesses need to ensure their RMM solution meets data security and compliance requirements. Solutions: Choose an RMM provider with strong security measures and compliance certifications, and implement appropriate data security policies.
Future Trends in RMM Software: Software Rmm
The RMM landscape is constantly evolving, driven by advancements in technology and the ever-changing needs of businesses. Several emerging trends are shaping the future of RMM, promising to enhance efficiency, security, and user experience.
The Rise of Artificial Intelligence and Machine Learning
AI and ML are playing an increasingly important role in RMM solutions. By leveraging these technologies, RMM software can automate tasks, improve decision-making, and enhance security posture.
- Predictive Maintenance: AI algorithms can analyze historical data on device performance and identify potential issues before they occur. This proactive approach minimizes downtime and reduces maintenance costs. For example, an RMM solution might use AI to predict when a hard drive is nearing failure based on factors like read/write speeds, temperature, and SMART data.
- Threat Detection and Response: ML algorithms can be trained to detect suspicious activity and identify potential threats in real-time. This enables RMM software to proactively block attacks and mitigate risks. For instance, an RMM solution might use ML to identify unusual network traffic patterns or suspicious file downloads, triggering an automated response to quarantine the affected device.
- Automated Patching and Updates: AI can streamline the patching process by identifying critical updates and automatically deploying them to devices. This reduces the risk of vulnerabilities and ensures systems are always up-to-date. For example, an RMM solution might use AI to prioritize patching based on the severity of the vulnerability and the likelihood of exploitation.
Ultimate Conclusion
In conclusion, Software RMM is an essential tool for any organization that wants to optimize its IT infrastructure, enhance security, and improve overall efficiency. By leveraging the power of remote monitoring, automation, and proactive management, businesses can achieve significant cost savings, reduce downtime, and ensure a secure and reliable IT environment. As technology continues to evolve, RMM solutions are poised to become even more sophisticated and integrated into the fabric of modern businesses, offering a powerful pathway to a future where IT operates seamlessly and securely.
Software RMM, or Remote Monitoring and Management, is a powerful tool for managing and securing IT infrastructure. If you need a robust graphics design solution for your projects, consider downloading CorelDraw X7, which can be found at download coreldraw x7.
With a comprehensive suite of features, CorelDraw X7 can be seamlessly integrated into your RMM strategy to ensure optimal performance and efficiency across your entire IT environment.