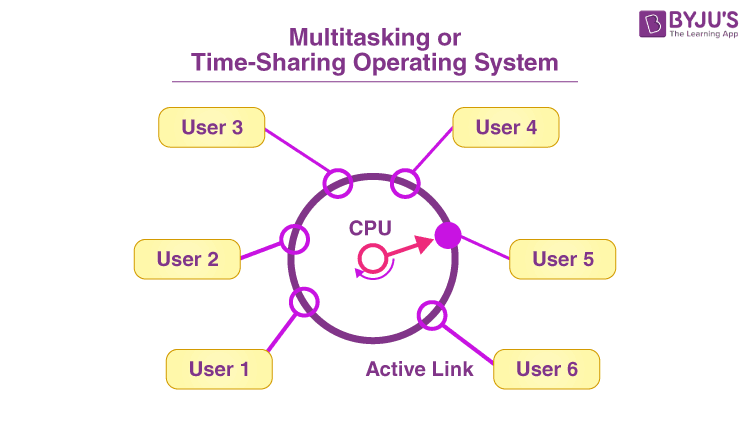
Time sharing operating system – Time-sharing operating systems revolutionized computing by allowing multiple users to share a single computer simultaneously. This innovation, born from the need to maximize expensive hardware resources, has profoundly shaped the landscape of modern computing.
Table of Contents
The concept of time-sharing emerged in the 1960s as a solution to the limitations of batch processing systems. Early pioneers like the Compatible Time-Sharing System (CTSS) and Multics demonstrated the feasibility of sharing a computer’s resources among multiple users, paving the way for the development of operating systems like UNIX and later, Windows and macOS.
Introduction to Time-Sharing Operating Systems
Time-sharing operating systems are a fundamental concept in modern computing, allowing multiple users to share a single computer system simultaneously. These systems divide the processor’s time among various tasks or users, creating the illusion that each user has exclusive access to the machine.
This approach revolutionized computing, enabling efficient resource utilization and user productivity.
History of Time-Sharing Systems
The development of time-sharing systems traces back to the early days of computing, with significant milestones and influential systems shaping its evolution.
- Early Concepts (1950s): The concept of time-sharing emerged in the 1950s, with researchers exploring ways to improve computer utilization and efficiency. Early ideas included using multiple programs simultaneously, but technical limitations and cost constraints hindered their implementation.
- MIT Compatible Time-Sharing System (CTSS) (1961): Developed at MIT, CTSS was one of the first successful implementations of a time-sharing system. It allowed multiple users to access a single IBM 7090 mainframe, paving the way for future developments.
- Project MAC (1963): Building upon the success of CTSS, MIT’s Project MAC focused on further research and development of time-sharing technologies. It led to the creation of the Multics operating system, which influenced many subsequent systems.
- Multics (1969): A pioneering time-sharing system developed jointly by MIT, Bell Labs, and General Electric, Multics introduced innovative concepts like hierarchical file systems and virtual memory. Although commercially unsuccessful, its influence on later systems, such as Unix, is undeniable.
- Unix (1970s): Developed at Bell Labs, Unix became a highly influential operating system that adopted key principles from Multics. It popularized time-sharing concepts and paved the way for modern operating systems.
Fundamental Principles of Time-Sharing
Time-sharing systems are based on fundamental principles that enable resource sharing, multitasking, and user interaction.
- Resource Sharing: Time-sharing systems allow multiple users to share the same physical resources, such as the CPU, memory, and peripherals. This sharing is made possible through techniques like time slicing, where the CPU’s time is divided into small intervals, and each user gets a portion of these intervals.
- Multitasking: Time-sharing systems enable multitasking, allowing multiple programs or tasks to run concurrently. This concurrency is achieved by rapidly switching between different tasks, giving the illusion of simultaneous execution.
- User Interaction: Time-sharing systems facilitate user interaction through the use of terminals or graphical interfaces. Users can interact with the system, run programs, and access data simultaneously, enhancing productivity and user experience.
Key Concepts and Features
Time-sharing operating systems are designed to allow multiple users to share a single computer system concurrently. This section delves into the key concepts and features that enable this shared resource utilization.
Time Slicing
Time slicing is a fundamental concept in time-sharing systems. It involves dividing the processor’s time into small intervals called “time slices” and allocating each time slice to a different user process. By rapidly switching between processes, the illusion of simultaneous execution is created, even though only one process can run at a time.
- Each process gets a fixed amount of time to execute before being interrupted and switched to another process. This ensures that no single process monopolizes the CPU, allowing fair sharing of resources.
- The time slice duration is typically very short, ranging from milliseconds to a few hundred milliseconds. This rapid switching creates the illusion of parallelism, where multiple users feel like they have dedicated access to the system.
Scheduling Algorithms
Scheduling algorithms play a crucial role in managing and allocating processor time among users. These algorithms determine the order in which processes are executed and how much time each process receives.
- First-Come, First-Served (FCFS): This algorithm executes processes in the order they arrive in the ready queue. While simple, it can lead to long waiting times for processes that arrive later.
- Shortest Job First (SJF): This algorithm prioritizes processes with shorter execution times, minimizing the average waiting time. However, it requires knowledge of the process execution time beforehand, which is not always possible.
- Priority Scheduling: This algorithm assigns priorities to processes, with higher-priority processes receiving more processor time. It allows for the prioritization of critical or time-sensitive tasks but can lead to starvation of low-priority processes.
- Round-Robin: This algorithm is commonly used in time-sharing systems. It assigns a fixed time slice to each process and cycles through the ready queue, giving each process a turn. This ensures fair allocation of CPU time and prevents starvation.
Virtual Memory
Virtual memory is a memory management technique that allows processes to access more memory than physically available. This is achieved by using secondary storage (e.g., hard disk) as an extension of the main memory.
- Processes are divided into pages, which are swapped between main memory and secondary storage as needed. This allows multiple processes to share the limited main memory without interfering with each other.
- Virtual memory significantly enhances the efficiency of time-sharing systems by allowing more processes to run concurrently than the physical memory can hold. It also simplifies memory management for programmers, as they can assume they have access to a larger memory space than physically available.
Memory Protection
Memory protection is a crucial feature in time-sharing systems. It ensures that processes cannot access or modify the memory space of other processes, protecting user data and preventing system instability.
- Memory protection mechanisms, such as memory segmentation and paging, establish boundaries between different processes. This prevents accidental or malicious access to sensitive information and ensures that processes operate in isolated memory spaces.
- Memory protection is essential for maintaining system stability and preventing crashes caused by one process corrupting the memory of another. It also enhances security by isolating processes from each other and preventing unauthorized access to data.
Architecture and Components
A time-sharing operating system is structured to efficiently manage and share system resources among multiple users. The core components include the kernel, system calls, and user processes.
The kernel acts as the heart of the operating system, responsible for managing all system resources and controlling access to hardware. It provides a secure and controlled environment for user processes to execute without interfering with each other.
Kernel
The kernel is the core of the operating system, responsible for managing all system resources and controlling access to hardware. It acts as an intermediary between user processes and the hardware, ensuring that resources are allocated and used efficiently.
The kernel’s primary functions include:
- Memory Management: The kernel allocates and manages memory for different processes, ensuring that they do not interfere with each other’s memory spaces. It employs techniques like paging and segmentation to divide memory into smaller units and assign them to processes.
- Process Management: The kernel manages the creation, scheduling, and termination of processes. It determines which processes are allowed to run and for how long, using scheduling algorithms to ensure fairness and efficiency.
- File System Management: The kernel manages the file system, including file creation, deletion, and access control. It provides a hierarchical structure for organizing files and directories, enabling users to manage their data efficiently.
- Device Management: The kernel manages all hardware devices connected to the system, including disk drives, printers, and network interfaces. It provides a standardized interface for user processes to interact with these devices.
- Security Management: The kernel enforces security policies, ensuring that unauthorized users cannot access sensitive system resources or data. It manages user accounts, permissions, and access control mechanisms to maintain system integrity.
System Calls
System calls are the interface between user processes and the kernel. They allow user processes to request services from the kernel, such as accessing hardware, creating files, or managing memory.
System calls provide a controlled and secure way for user processes to interact with the kernel. They act as a gateway, ensuring that only authorized requests are passed to the kernel, preventing unauthorized access to system resources.
Examples of System Calls
Here are some common system calls used in time-sharing systems:
- read(): Reads data from a file or device.
- write(): Writes data to a file or device.
- fork(): Creates a new process.
- exec(): Loads and executes a new program.
- open(): Opens a file or device.
- close(): Closes a file or device.
- getpid(): Returns the process ID of the current process.
- wait(): Waits for a child process to terminate.
Advantages and Disadvantages of Time-Sharing
Time-sharing operating systems revolutionized computing by allowing multiple users to share a single computer system simultaneously. This concept has significantly impacted how we interact with computers and has led to the development of modern multi-user systems. However, like any technology, time-sharing comes with its own set of advantages and disadvantages.
Advantages of Time-Sharing
Time-sharing offers numerous advantages that have made it a popular choice for various applications. These benefits include:
- Improved Resource Utilization: Time-sharing allows for efficient resource utilization by sharing the CPU, memory, and other resources among multiple users. This approach significantly reduces idle time, as the CPU is always busy processing tasks for different users.
- Increased Productivity: Users can access the system simultaneously, allowing them to work independently and complete tasks faster. This increased productivity is particularly valuable in environments where multiple users need to collaborate on projects.
- Enhanced Responsiveness: Time-sharing provides a more responsive user experience by quickly switching between different users’ tasks. This quick switching minimizes waiting time and allows users to feel like they have exclusive access to the system, even though they are sharing it with others.
- Cost-Effectiveness: Sharing resources among multiple users reduces the overall cost of computing, as the hardware and software costs are distributed across a larger user base. This makes time-sharing a cost-effective solution for organizations and individuals with limited resources.
Disadvantages of Time-Sharing
While time-sharing offers many benefits, it also presents some challenges that need to be addressed. These disadvantages include:
- Potential Performance Degradation: Sharing resources can lead to performance degradation if the system is overloaded with too many users or tasks. This can result in slower response times and increased waiting times for users.
- Security Risks: Time-sharing systems can be vulnerable to security breaches if proper security measures are not in place. Malicious users could potentially access or modify other users’ data or even disrupt the system’s operation.
- Sophisticated System Management: Time-sharing systems require sophisticated management tools and techniques to ensure efficient resource allocation and user management. This can be a complex task, requiring specialized skills and expertise.
Comparison with Other Operating System Models
Time-sharing systems offer a distinct set of advantages and disadvantages compared to other operating system models.
Comparison with Batch Processing
- Batch Processing: This model involves executing jobs sequentially, without user interaction. It is efficient for large-scale tasks but lacks interactivity and responsiveness. Time-sharing offers a more interactive and responsive environment, making it suitable for tasks requiring immediate feedback and user interaction.
Comparison with Real-Time Systems
- Real-Time Systems: These systems are designed for applications where timely response is critical, such as industrial control systems. They prioritize immediate task execution over resource sharing. Time-sharing systems prioritize resource sharing and may not be suitable for applications with strict timing requirements.
Examples of Time-Sharing Operating Systems
Time-sharing operating systems have played a pivotal role in the evolution of computing, enabling efficient resource utilization and interactive computing experiences. This section explores some of the most influential time-sharing operating systems throughout history, examining their key features, contributions, and design choices.
UNIX
UNIX, developed at Bell Labs in the early 1970s, is a foundational time-sharing operating system that has had a profound impact on the computing landscape. Its key features include:
- Hierarchical file system: UNIX introduced a hierarchical file system, organizing files and directories in a tree-like structure, simplifying navigation and management.
- Command-line interface: UNIX provided a powerful command-line interface (CLI) for interacting with the system, enabling users to execute commands and manage files efficiently.
- Portability: Designed with portability in mind, UNIX could be adapted to run on different hardware platforms, fostering its widespread adoption.
- Multitasking and multi-user support: UNIX supported multitasking and multi-user environments, allowing multiple users to share the system’s resources simultaneously.
UNIX’s design philosophy emphasized simplicity, modularity, and portability, making it a highly influential operating system. It has served as the basis for many other operating systems, including Linux, macOS, and Solaris.
Multics
Multics, developed jointly by MIT, Bell Labs, and General Electric in the 1960s, was an ambitious time-sharing operating system that introduced several innovative concepts.
- Virtual memory: Multics pioneered the concept of virtual memory, allowing programs to access more memory than physically available, improving performance and efficiency.
- Segmented addressing: It implemented segmented addressing, dividing memory into segments, enabling efficient memory management and protection.
- Security features: Multics emphasized security, incorporating features like access control lists and ring protection to safeguard system resources.
Multics’ innovative features influenced the development of subsequent operating systems, particularly in the areas of memory management and security.
IBM OS/360
IBM OS/360, released in 1964, was a groundbreaking time-sharing operating system designed for IBM’s System/360 mainframe computers.
- Batch processing and time-sharing capabilities: OS/360 supported both batch processing and time-sharing, enabling efficient execution of both large and interactive tasks.
- Multiprogramming: It allowed multiple programs to run concurrently, maximizing resource utilization.
- Virtual storage: OS/360 implemented virtual storage, allowing programs to access more memory than physically available, improving performance and efficiency.
- System/360 architecture: OS/360 was designed specifically for the System/360 architecture, leveraging its capabilities to provide robust and efficient operations.
IBM OS/360 established a standard for mainframe operating systems, influencing the design of subsequent systems and solidifying IBM’s dominance in the mainframe market.
Other Notable Time-Sharing Operating Systems
Several other time-sharing operating systems contributed significantly to the evolution of computing. These include:
- CTSS (Compatible Time-Sharing System): Developed at MIT in the early 1960s, CTSS was one of the first time-sharing operating systems, demonstrating the feasibility of interactive computing.
- CP/CMS (Control Program/Conversational Monitor System): Developed by IBM, CP/CMS was a time-sharing operating system for the IBM System/360, offering a more interactive environment than OS/360.
- TENEX: Developed at Bolt, Beranek and Newman (BBN) in the late 1960s, TENEX was a time-sharing operating system known for its advanced features, including virtual memory and a sophisticated file system.
These systems, along with others, paved the way for modern operating systems, demonstrating the potential of time-sharing for efficient resource utilization and interactive computing.
Modern Applications of Time-Sharing
Time-sharing principles, initially designed for resource optimization on mainframe computers, have evolved to become fundamental in modern operating systems and computing environments. These principles are now seamlessly integrated into the core functionality of various operating systems and cloud computing platforms, enabling efficient resource utilization and enabling a wide range of applications.
Time-Sharing in Modern Operating Systems
Modern operating systems like Windows, macOS, and Linux employ time-sharing to manage multiple processes running concurrently on a single processor. This allows users to run various applications simultaneously, such as browsing the web, editing documents, and listening to music, without noticeable performance degradation.
- Process Scheduling: Time-sharing relies on a process scheduler, which allocates CPU time to different processes in a fair and efficient manner. This scheduler ensures that each process receives a slice of CPU time, preventing any single process from monopolizing the processor and causing other processes to stall.
- Context Switching: When a process’s time slice expires, the operating system performs a context switch, saving the state of the current process and loading the state of the next process. This allows for a smooth transition between processes, providing the illusion of parallel execution.
- Multitasking: Time-sharing enables multitasking, allowing users to run multiple applications concurrently. This significantly enhances user productivity by allowing them to perform various tasks simultaneously.
Time-Sharing in Cloud Computing and Distributed Systems
Time-sharing plays a crucial role in cloud computing and distributed systems, where resources are shared across multiple virtual machines (VMs) or containers. Cloud providers leverage time-sharing to optimize resource utilization and provide cost-effective solutions for various applications.
- Virtualization: Cloud computing relies heavily on virtualization, where physical hardware is partitioned into multiple virtual machines. Time-sharing principles are used to allocate CPU time and other resources to these VMs, ensuring efficient resource utilization and allowing multiple users to share the same hardware.
- Containerization: Containerization, a lightweight virtualization technology, utilizes time-sharing to manage containers. Containers package applications and their dependencies, enabling them to run consistently across different environments. Time-sharing ensures that multiple containers running on a single host system share CPU time and other resources efficiently.
- Resource Sharing: Time-sharing is essential for sharing resources in distributed systems, where applications and data are spread across multiple computers. This enables load balancing and fault tolerance, ensuring high availability and performance even in the presence of failures.
Real-World Applications of Time-Sharing
Time-sharing is a cornerstone of many real-world applications, enabling efficient resource utilization and scalability for various services.
- Web Servers: Web servers handle numerous client requests concurrently, using time-sharing to allocate CPU time to each request. This ensures that multiple users can access a website simultaneously without experiencing delays.
- Databases: Database systems use time-sharing to manage multiple queries and transactions concurrently. This allows for efficient data processing and retrieval, even when multiple users are accessing the database simultaneously.
- Enterprise Applications: Enterprise applications, such as customer relationship management (CRM) systems and enterprise resource planning (ERP) systems, rely on time-sharing to handle multiple user requests and data processing tasks concurrently. This ensures high performance and responsiveness for users.
Future Trends in Time-Sharing
Time-sharing operating systems are constantly evolving to meet the demands of increasingly complex computing environments. Advancements in hardware, software, and network technologies are driving the development of new and innovative approaches to time-sharing, paving the way for more efficient, scalable, and secure systems.
Multi-Core Processors and Parallel Computing
The rise of multi-core processors has significantly impacted time-sharing systems. These processors allow multiple tasks to run concurrently on different cores, improving overall system performance. Parallel computing, a technique that leverages multiple processors to execute tasks simultaneously, further enhances the capabilities of time-sharing systems. By effectively distributing workloads across multiple cores, parallel computing enables faster execution times and increased throughput.
Virtualization
Virtualization plays a crucial role in modern time-sharing systems. It allows for the creation of virtual machines (VMs) that run on top of a physical host machine. Each VM can have its own operating system and resources, enabling efficient resource allocation and isolation. Virtualization simplifies system management, improves resource utilization, and enhances security by isolating applications from each other.
Cloud Computing
Cloud computing has revolutionized the way time-sharing systems are deployed and managed. Cloud platforms provide on-demand access to computing resources, including processors, storage, and networking. This allows users to scale their time-sharing systems dynamically based on their needs, eliminating the need for significant upfront investments in hardware. Cloud-based time-sharing systems offer flexibility, scalability, and cost-effectiveness.
Challenges and Opportunities in Scaling Time-Sharing Systems, Time sharing operating system
Scaling time-sharing systems to handle increasing workloads and user demands presents several challenges. Managing resource allocation efficiently, ensuring system stability and security, and maintaining performance under heavy loads are critical considerations.
- Resource Allocation: As workloads grow, ensuring fair and efficient allocation of resources, such as CPU time, memory, and disk space, becomes increasingly challenging. Time-sharing systems need to adapt their resource allocation algorithms to handle the dynamic nature of modern workloads.
- System Stability: Scaling up time-sharing systems can lead to increased complexity and potential instability. Robust mechanisms are needed to prevent system crashes and maintain consistent performance, even under high load conditions.
- Security: With more users and applications sharing the system, security becomes paramount. Time-sharing systems need to implement robust security measures to protect against unauthorized access, data breaches, and other security threats.
Potential Future Directions of Time-Sharing Systems
Time-sharing systems are continuously evolving to address emerging challenges and opportunities. Future trends include:
- More Efficient Resource Allocation Mechanisms: Developing advanced resource allocation algorithms that can dynamically adapt to changing workloads and ensure optimal resource utilization.
- Enhanced Security: Implementing sophisticated security features, such as advanced authentication, encryption, and access control mechanisms, to protect sensitive data and prevent unauthorized access.
- Integration with Artificial Intelligence (AI): Utilizing AI algorithms to optimize resource allocation, improve performance, and enhance system security.
Final Thoughts: Time Sharing Operating System
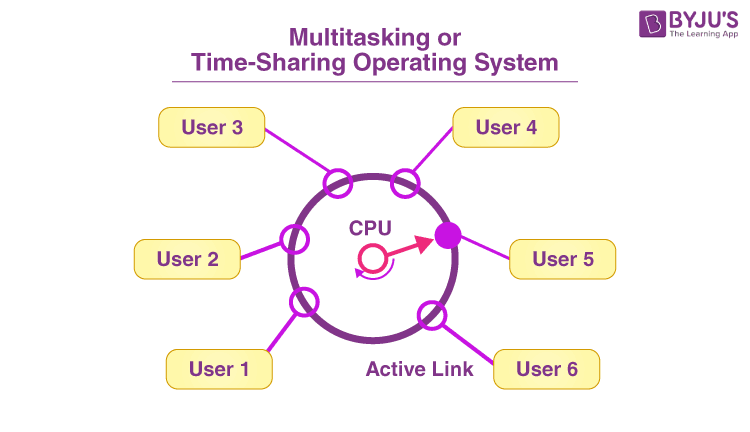
Time-sharing operating systems have evolved significantly over the years, but their core principles remain relevant in today’s world. From the early days of mainframe computers to the cloud-based platforms of today, time-sharing has enabled us to access computing power more efficiently and effectively. As technology continues to advance, time-sharing will undoubtedly play a crucial role in shaping the future of computing.
Time-sharing operating systems, like those found on mainframes in the past, allowed multiple users to share a single computer simultaneously. This concept of resource sharing has evolved, with modern applications like fonelab offering similar capabilities, allowing users to access and manage their mobile devices remotely.
The core principle of time-sharing remains relevant, with applications like fonelab demonstrating its continued influence in the digital landscape.