Windows Firewall, the unsung hero of your digital world, silently guards your computer from the constant barrage of online threats. It acts as a digital gatekeeper, carefully scrutinizing incoming and outgoing network traffic, allowing only trusted connections to pass through.
Table of Contents
From its humble beginnings as a basic security feature, Windows Firewall has evolved into a sophisticated tool, offering a range of customization options and advanced features. This comprehensive guide delves into the workings of Windows Firewall, exploring its functionality, configuration, and best practices for ensuring robust security.
Introduction to Windows Firewall
The Windows Firewall is a built-in security feature in Microsoft Windows operating systems that helps protect your computer from unauthorized access and malicious attacks. It acts as a barrier between your computer and the internet, allowing only authorized traffic to pass through.
The Windows Firewall works by examining incoming and outgoing network traffic and blocking any traffic that doesn’t meet the defined rules. These rules can be configured by the user to allow or block specific applications, ports, or network addresses.
Types of Firewalls
Firewalls can be categorized based on their implementation and location:
- Software Firewalls: These are software programs installed on a device, such as a computer or smartphone, to filter network traffic. The Windows Firewall is an example of a software firewall.
- Hardware Firewalls: These are physical devices that are connected to a network and filter traffic at the network level. They are often used in businesses and organizations to protect their entire network.
- Next-Generation Firewalls (NGFWs): These are advanced firewalls that provide more comprehensive security features, such as intrusion prevention, application control, and threat intelligence. They are often used in enterprise environments.
History of the Windows Firewall
The Windows Firewall has evolved significantly since its first introduction in Windows XP Service Pack 2 (SP2) in 2004. Here are some key milestones:
- Windows XP SP2 (2004): The first version of the Windows Firewall was introduced, offering basic protection against incoming network traffic.
- Windows Vista (2006): The Windows Firewall was enhanced with improved features, including support for outgoing traffic filtering and more granular control over network connections.
- Windows 7 (2009): The Windows Firewall received further improvements, including support for IPv6 and a simplified user interface.
- Windows 8 (2012): The Windows Firewall was integrated with Windows Defender to provide comprehensive protection against malware and other threats.
- Windows 10 (2015): The Windows Firewall continued to evolve with new features, including support for Windows Defender Firewall Control and enhanced security for cloud-based applications.
How Windows Firewall Works
The Windows Firewall is a crucial security component of the Windows operating system, acting as a barrier between your computer and the outside world. It analyzes incoming and outgoing network traffic, blocking potentially harmful connections while allowing legitimate traffic to pass through.
Firewall Rules
Firewall rules are the foundation of how the Windows Firewall operates. These rules define which network traffic is allowed or blocked, based on various factors like the source and destination IP addresses, ports, applications, and protocols.
The Windows Firewall comes with a set of predefined rules, but you can customize them to fit your specific needs. You can create new rules, modify existing ones, or disable specific rules to control network access.
For example, you might create a rule to block all incoming traffic on port 22, which is commonly used for SSH connections. This rule would prevent unauthorized remote access to your computer.
Blocking Incoming Traffic
When a network connection attempt is made to your computer, the Windows Firewall examines the incoming traffic against its predefined rules. If the traffic matches a rule that allows it, the connection is established. However, if the traffic matches a rule that blocks it, the connection is denied.
Blocking Outgoing Traffic
The Windows Firewall also monitors outgoing traffic from your computer. If a rule blocks outgoing traffic, the connection is denied. This helps prevent malicious software from sending data to external servers or accessing unauthorized resources.
Firewall Rules and Policies
Firewall rules are the heart of Windows Firewall’s functionality, determining what traffic is allowed in and out of your system. They act as specific instructions, telling the firewall how to handle network traffic based on various factors like source and destination IP addresses, ports, protocols, and applications.
Firewall Rule Types
Firewall rules are categorized based on their direction and purpose. Understanding these types helps you create tailored rules that align with your security needs.
- Inbound Rules: These rules control incoming network traffic, determining which applications and services can be accessed from outside your computer. They are crucial for protecting your system from malicious connections or unauthorized access attempts.
- Outbound Rules: These rules govern outgoing network traffic, controlling which applications and services can initiate connections to external resources. They are useful for restricting access to specific websites, preventing malware from communicating with command-and-control servers, or limiting bandwidth usage.
Creating and Managing Firewall Rules, Windows firewall
You can manage firewall rules through the Windows Firewall with Advanced Security interface, a powerful tool that provides granular control over network traffic. Here’s a general overview of the process:
- Access the Windows Firewall with Advanced Security: You can access this interface through the Control Panel or by searching for “Windows Firewall with Advanced Security” in the Windows search bar.
- Create New Rules: The interface provides a wizard-like experience to create new firewall rules. You’ll need to specify details like rule type (inbound or outbound), program or service, protocol, ports, and action (allow, block, or ask).
- Edit Existing Rules: You can modify existing rules to change their behavior or adjust their settings. This flexibility allows you to adapt your firewall configuration as your network environment evolves.
- Delete Rules: If a rule is no longer necessary, you can delete it to simplify your firewall configuration and ensure optimal performance.
Common Firewall Rule Configurations
Here are some common examples of firewall rule configurations:
- Blocking Specific Ports: You can create rules to block access to specific ports, such as port 21 (FTP) or port 22 (SSH), to prevent unauthorized connections to these services. This is particularly useful for hardening your system against known vulnerabilities.
- Allowing Specific Applications: You can create rules to allow specific applications to communicate with external resources. For instance, you might allow your web browser to access the internet while blocking other applications from initiating outbound connections. This approach helps to restrict potential attack vectors and improve overall security.
- Restricting Outbound Traffic: You can create rules to limit outgoing network traffic, preventing applications from connecting to specific websites or IP addresses. This is useful for controlling bandwidth usage, preventing data leakage, or restricting access to potentially malicious websites.
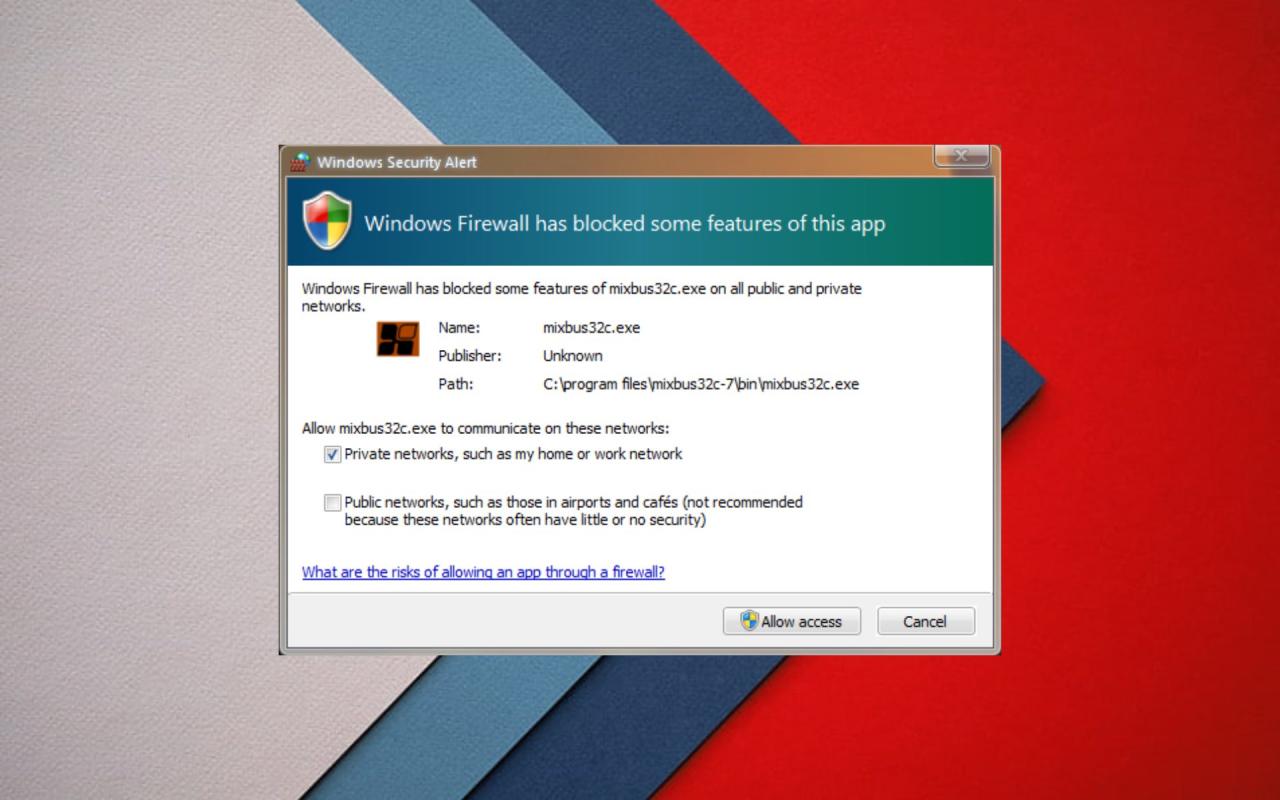
Firewall Exceptions and Ports
Windows Firewall is designed to protect your computer from unauthorized access, but sometimes you need to allow specific applications or services to communicate with the outside world. This is where firewall exceptions come in. Firewall exceptions are rules that tell the firewall to allow certain types of traffic to pass through, even though it would normally be blocked.
Opening specific ports for applications is essential because it allows them to function properly. Ports are virtual channels that applications use to communicate with each other over a network. For example, a web browser uses port 80 to communicate with web servers, and an email client uses port 25 to send and receive emails.
Common Ports and Associated Applications
Many common applications use specific ports to communicate. Here are a few examples:
- Port 80: Used for standard HTTP traffic (web browsing).
- Port 443: Used for HTTPS traffic (secure web browsing).
- Port 21: Used for FTP (File Transfer Protocol).
- Port 22: Used for SSH (Secure Shell) remote access.
- Port 25: Used for SMTP (Simple Mail Transfer Protocol) email sending.
- Port 110: Used for POP3 (Post Office Protocol 3) email receiving.
- Port 143: Used for IMAP (Internet Message Access Protocol) email receiving.
- Port 53: Used for DNS (Domain Name System) name resolution.
- Port 3389: Used for RDP (Remote Desktop Protocol) remote access.
Firewall Security Best Practices: Windows Firewall
The Windows Firewall is a crucial component of your computer’s security, and configuring it properly can significantly enhance your protection against online threats. By implementing best practices, you can maximize the effectiveness of your firewall and safeguard your system from malicious attacks.
Keeping the Firewall Enabled and Updated
It is essential to keep the Windows Firewall enabled at all times to ensure that your computer is protected from unauthorized access and malicious software. The firewall acts as a barrier between your computer and the internet, preventing unauthorized connections and blocking potentially harmful programs. Disabling the firewall weakens your security posture and exposes your system to various risks.
- Regularly check for and install updates for the Windows Firewall. These updates often include security patches and improvements that address vulnerabilities and enhance the firewall’s effectiveness.
- Configure the firewall to automatically download and install updates. This ensures that your firewall is always running with the latest security features.
Understanding the Importance of Firewall Rules
Firewall rules are essential for controlling which programs and services can access your computer and the internet. These rules act as filters, allowing specific connections while blocking others. Carefully defining firewall rules can enhance security and prevent unauthorized access to your system.
- Create specific rules for programs that need to access the internet. This allows you to control which programs can connect to the network and prevent unauthorized access.
- Review existing firewall rules regularly to ensure they are still relevant and appropriate for your current needs. Remove or modify rules that are no longer necessary.
Avoiding Unnecessary Firewall Exceptions
Firewall exceptions allow specific programs or services to bypass the firewall’s protection. While exceptions can be useful for legitimate programs, they can also create security vulnerabilities if not carefully managed.
- Avoid creating exceptions for programs you don’t trust or understand. Only create exceptions for programs that you are certain are safe and necessary for your work or entertainment.
- Regularly review firewall exceptions and remove any that are no longer needed. This helps to minimize the attack surface and reduce the risk of unauthorized access.
Understanding the Risks of Disabling the Firewall
Disabling the Windows Firewall weakens your security posture and exposes your computer to various risks. Without the firewall’s protection, malicious software can easily access your system, steal your personal information, and cause significant damage.
- Malicious software can exploit vulnerabilities in your system and gain unauthorized access to your data. This can lead to data theft, identity theft, and financial losses.
- Hackers can use your computer to launch attacks against other systems. This can damage your reputation and expose you to legal consequences.
- Your computer can become infected with viruses, malware, and other harmful programs that can corrupt your files, slow down your system, and compromise your privacy.
Troubleshooting Firewall Issues
Troubleshooting firewall issues can be a challenging task, but it’s essential for maintaining a secure network. This section provides a step-by-step guide to help you identify and resolve common firewall problems.
Identifying Common Firewall Problems
Common firewall problems can manifest in various ways, such as:
- Inability to access specific websites or online services.
- Difficulty connecting to a network or the internet.
- Receiving error messages related to network connectivity.
- Slow network performance.
- Suspicious activity detected by the firewall.
Troubleshooting Steps
Here’s a step-by-step guide to troubleshooting common firewall issues:
- Check Network Connectivity: Ensure your network connection is working correctly. Verify that your internet connection is active and that your network cable is properly plugged in. You can test your network connectivity by visiting a website like google.com.
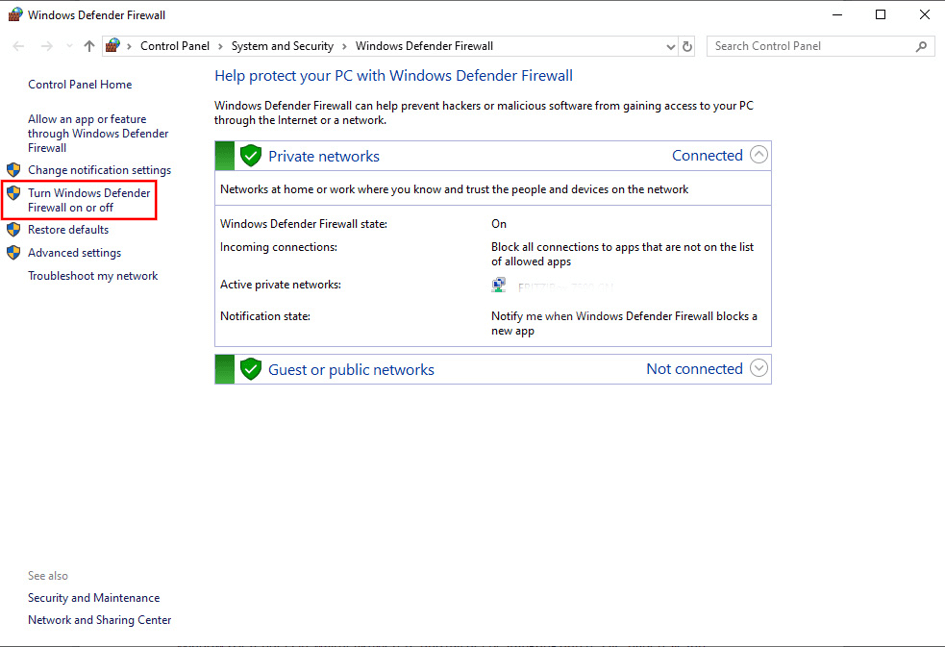
- Verify Firewall Status: Ensure that the Windows Firewall is enabled. You can check this by going to Control Panel > System and Security > Windows Firewall. If the firewall is disabled, enable it and try again.
- Review Firewall Rules: Examine the firewall rules to identify any rules that might be blocking access to the website or service you’re trying to reach. You can access firewall rules by going to Control Panel > System and Security > Windows Firewall > Advanced settings.
- Temporarily Disable Firewall: If you’re still experiencing issues, temporarily disable the firewall to see if it resolves the problem. However, it’s important to note that disabling the firewall compromises your system’s security. Only do this as a temporary troubleshooting measure.
- Check for Firewall Conflicts: If you have multiple security software programs installed, there might be conflicts between their firewall rules. Try disabling other security software temporarily to see if it resolves the issue.
- Update Firewall and Operating System: Ensure your firewall and operating system are up-to-date. Updates often include security patches and bug fixes that can address firewall issues.
- Run Network Troubleshooter: Windows provides a built-in network troubleshooter that can help identify and fix common network problems. You can access the troubleshooter by going to Control Panel > System and Security > Troubleshooting > Network and Internet.
Common Error Messages and Solutions
Here are some common error messages you might encounter when troubleshooting firewall issues and their possible solutions:
| Error Message | Solution |
|---|---|
| “Windows Firewall is blocking some features of this program.” | Allow the program through the firewall by creating a new rule or modifying existing rules. |
| “Error connecting to the server.” | Check your network connection and verify that the server is online. Ensure that the firewall is not blocking access to the server. |
| “Access denied.” | This error message could indicate that the firewall is blocking access to a specific website or service. Check the firewall rules and ensure that the website or service is allowed. |
Resolving Firewall Rule Conflicts
If you have multiple security software programs installed, there might be conflicts between their firewall rules. Here are some tips for resolving firewall rule conflicts:
- Prioritize Firewall Rules: Ensure that the rules of your primary firewall are given higher priority than those of other security software programs. This helps prevent conflicts and ensures that the most important rules are enforced.
- Disable Conflicting Rules: Temporarily disable firewall rules from other security software programs to see if it resolves the issue. If disabling a specific rule resolves the conflict, consider keeping it disabled or configuring it to allow access to the necessary resources.
- Review Firewall Settings: Carefully review the settings of all your firewall programs to ensure that there are no overlapping or conflicting rules. If you find any conflicts, adjust the settings accordingly.
Advanced Firewall Features
The Windows Firewall offers advanced features that enhance security beyond its basic functionality. These features provide more granular control over network traffic and application behavior, enabling you to tailor your firewall settings to meet specific security needs.
Network Isolation
Network isolation, a crucial security feature, separates your computer from the network. It prevents unauthorized access to your data and resources by limiting communication between your computer and other devices on the network.
- Private Networks: When connected to a private network, such as your home network, network isolation can restrict communication between your computer and other devices on the same network. This can be useful if you want to prevent other devices from accessing sensitive data on your computer.
- Public Networks: On public networks, like those found in coffee shops or airports, network isolation is particularly important. It helps prevent unauthorized access to your computer and data by limiting communication with other devices on the network.
To configure network isolation, open Windows Firewall settings and enable the “Network isolation” option. You can then choose to restrict communication to specific devices or applications.
Application Control
Application control allows you to control which applications can access the network. This feature enables you to prevent potentially malicious applications from communicating with external servers or accessing sensitive data.
- Allow or Block Applications: You can create rules that allow or block specific applications from accessing the network. For example, you can block a particular application from connecting to the internet or restrict its communication to specific websites.
- Application Control Rules: Application control rules can be based on the application’s name, file path, or other criteria. You can also specify the type of network access allowed for each application, such as inbound, outbound, or both.
To configure application control, open Windows Firewall settings and access the “Application control” section. Here, you can create new rules, modify existing rules, or view the current application control settings.
Firewall Security Best Practices
- Keep Your Firewall Updated: Microsoft regularly releases updates for Windows Firewall to address security vulnerabilities. Ensure your firewall is up to date by installing the latest Windows updates.
- Review Firewall Rules: Regularly review your firewall rules to ensure they are still relevant and effective. Remove or modify rules that are no longer necessary.
- Use Strong Passwords: Protect your computer from unauthorized access by using strong passwords for your user accounts and network connections.
Windows Firewall in a Network Environment
In a networked environment, the Windows Firewall plays a crucial role in safeguarding your computer and network from unauthorized access and malicious threats. It acts as a barrier between your computer and the outside world, controlling the flow of network traffic and preventing unwanted connections. Understanding how the Windows Firewall interacts with other network security devices and how to configure it effectively is essential for maintaining a secure network.
Interaction with Other Network Security Devices
The Windows Firewall works in conjunction with other network security devices, such as routers and firewalls, to create a multi-layered security approach. Routers typically act as the first line of defense, filtering traffic at the network level and blocking access to unauthorized devices. Firewalls, including the Windows Firewall, provide an additional layer of protection by controlling traffic at the individual computer level.
- Routers: Routers operate at the network layer of the TCP/IP model, inspecting traffic based on IP addresses and ports. They can block traffic from specific IP addresses or prevent access to certain ports. The Windows Firewall complements the router by further filtering traffic based on applications, protocols, and other criteria.
- Firewalls: Firewalls, including the Windows Firewall, operate at the application layer of the TCP/IP model, providing more granular control over traffic. They can inspect traffic based on applications, protocols, and even the content of data packets. The Windows Firewall can be configured to work in conjunction with other firewalls, such as those deployed on a network perimeter or in a cloud environment.
Importance of Configuring Firewall Rules in a Network Environment
Configuring firewall rules is crucial for securing a network environment. Properly defined rules ensure that only authorized traffic is allowed to pass through the firewall, while blocking potentially malicious or unwanted connections. By creating specific rules, you can control which applications are allowed to access the internet, which ports are open for inbound and outbound connections, and which devices are allowed to connect to your network.
Best Practices for Firewall Deployment in a Network
Implementing a firewall effectively requires following best practices to ensure optimal security and performance.
- Define a Clear Security Policy: Establish a comprehensive security policy that Artikels the acceptable use of network resources, defines access control rules, and establishes guidelines for firewall configuration. This policy should be reviewed and updated regularly to reflect evolving security threats and network changes.
- Implement a Multi-Layered Security Approach: Utilize multiple security layers, including firewalls, antivirus software, intrusion detection systems, and user authentication mechanisms, to provide a comprehensive defense against threats.
- Regularly Review and Update Firewall Rules: As network requirements and security threats change, it is essential to regularly review and update firewall rules. This includes blocking outdated or unnecessary applications, enabling new applications that require network access, and adjusting rules based on new security vulnerabilities.
- Utilize Strong Passwords and Access Control: Protect firewall configuration settings with strong passwords and restrict access to authorized personnel only. This helps prevent unauthorized changes to firewall rules that could compromise security.
- Monitor Firewall Logs: Regularly review firewall logs to identify any suspicious activity or potential security breaches. This can help you detect and respond to threats before they cause significant damage.
- Implement Network Segmentation: Divide the network into smaller, isolated segments to limit the impact of security breaches. This can help prevent a single attack from compromising the entire network.
- Keep Firewall Software Updated: Regularly update firewall software to patch vulnerabilities and ensure that it is protected against the latest threats.
Security Considerations
While the Windows Firewall offers a robust layer of protection, it’s essential to acknowledge its limitations and potential vulnerabilities. Understanding these weaknesses allows you to implement additional security measures to enhance your overall network security.
Vulnerabilities and Limitations
The Windows Firewall, despite its effectiveness, is not impervious to all threats. Here are some key vulnerabilities and limitations to be aware of:
- Firewall Bypass: Malicious actors may exploit vulnerabilities in other software or operating system components to bypass the firewall altogether. This could involve using specific network protocols, exploiting zero-day vulnerabilities, or employing advanced techniques like code injection.
- Configuration Errors: Misconfigured firewall rules or exceptions can inadvertently expose your system to attacks. For example, allowing unnecessary ports or services to be accessible from the internet could create vulnerabilities.
- Limited Protection Against Internal Threats: The Windows Firewall primarily focuses on protecting against external threats. It may not effectively prevent malicious activity originating from within your network, such as malware installed on a compromised computer.
- Firewall Spoofing: Attackers can attempt to spoof their IP addresses or use other techniques to deceive the firewall into granting access. This can allow them to bypass security measures and gain unauthorized access to your system.
- Limited Real-Time Threat Detection: While the Windows Firewall can block known threats based on predefined rules, it may not be able to detect and respond to emerging or unknown threats in real-time.
Mitigating Vulnerabilities
To address these vulnerabilities and enhance your overall security, consider implementing the following measures:
- Regular Updates: Ensure that your operating system and all software applications are regularly updated to patch vulnerabilities and security flaws. This is crucial to stay ahead of attackers who may exploit known weaknesses.
- Strong Passwords: Use strong and unique passwords for all accounts, including administrative accounts. This reduces the risk of unauthorized access through brute-force attacks or password guessing.
- Multi-Factor Authentication: Enable multi-factor authentication (MFA) whenever possible. This adds an extra layer of security by requiring users to provide additional verification factors beyond their passwords, such as a code sent to their mobile device.
- Antivirus and Anti-Malware Software: Install and maintain robust antivirus and anti-malware software to detect and remove threats that may bypass the firewall. Regularly update these programs to ensure they are effective against the latest threats.
- Network Segmentation: If possible, segment your network into different zones with varying levels of security. This can help isolate sensitive data and systems from potential attacks. For example, you could create a separate zone for guest users or for critical infrastructure.
- Intrusion Detection and Prevention Systems (IDS/IPS): Consider implementing an intrusion detection and prevention system (IDS/IPS) to monitor network traffic for suspicious activity and block potential attacks. These systems can detect anomalies and patterns that may indicate malicious intent.
- Regular Security Audits: Conduct regular security audits to assess your network’s vulnerabilities and identify potential weaknesses. These audits can help you proactively address security risks and ensure that your firewall is properly configured.
- User Education: Train users about best security practices, such as avoiding suspicious links, being cautious about email attachments, and reporting any unusual activity. Educated users can play a crucial role in preventing security breaches.
Last Word
As the digital landscape grows increasingly complex, Windows Firewall remains a vital component of a comprehensive security strategy. By understanding its workings and implementing best practices, you can empower your computer with a robust shield against online threats, ensuring peace of mind in your digital endeavors.
Windows Firewall is a crucial component of your system’s security, preventing unauthorized access and potential threats. If you’re looking for a powerful and versatile audio editor, you can download Audacity for free here. After you’ve downloaded and installed Audacity, remember to check your firewall settings to ensure it’s not blocking the program from accessing the internet for updates or other necessary functions.
